6 Signs Your Phone Was Hacked
From holding conversations to paying for things, we use our smartphones for a wide range of applications in the modern day. This makes them a lucrative target for any bad actors to try and exploit. A little slip-up is all it would take for an attacker to get hold of your personal information, banking details, and private messages. Thankfully, both Android and iOS have matured significantly over the years when it comes to security.
When you think of the term "hacking," you're probably visualizing a hooded, mysterious being remotely sending lines of code to your phone and gaining "access to the mainframe," as Hollywood likes to call it. In reality, while there are unexpected ways your phone could be hacked, modern operating systems fare surprisingly well against such attempts. This can largely be attributed to technologies such as encryption and multi-factor authentication.
Instead of brute-forcing their way into a properly shielded smartphone, many hackers adopt what's called social engineering — which is a form of cyberattack that involves manipulating the victim's trust or behavior into giving up their credentials or one-time passwords. You may have heard of phishing, which is one of the most common kinds of social engineering attacks. Prevention is always better than cure, but if your phone's first line of defense fails, you should immediately start looking for signs of compromise. Unlike on computers, malware on smartphones isn't as easy to spot, but there are certain behavioral clues that can give it away.
Shady apps or pop-up advertisements
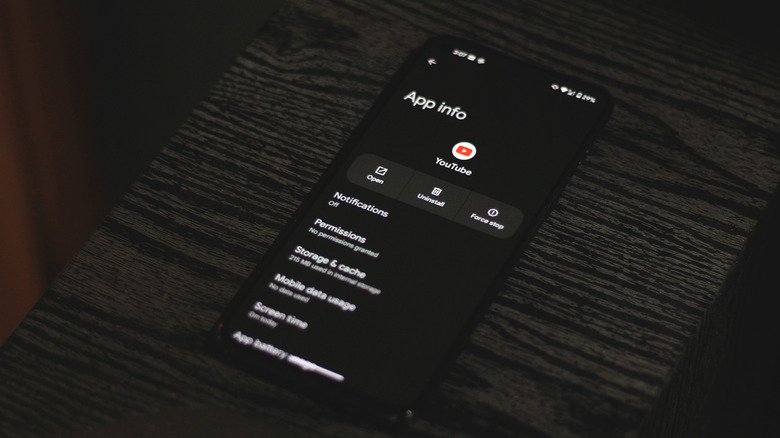
An unfamiliar app or service that you don't remember installing yourself is a major red flag and should always warrant your attention. Android is praised for the comparatively greater level of freedom in customization and app support it offers over iOS, and that's primarily due to its open-source nature. This lets users sideload apps pretty easily, but it is also what makes Android an easy target for malicious applications to slip through and take root.
There are several kinds of malware that attackers deploy, Trojans and adware being the most common for smartphones. Adware is generally served with the purpose of generating revenue for the attacker when you look at or unintentionally click on pop-up ads. This can make daily operations on your phone seem frustrating. Trojans, on the other hand, pose a more serious threat and may end up stealing sensitive personal information.
Regardless of the type of malware, if you notice a suspicious app installed on your phone, it's best to uninstall it right away. On Android, you can tap and hold on an app's icon and navigate to "App Info" to check the source of installation. If it's anything other than the Play Store, that means it's been sideloaded. You can use Android's built-in Google Play Protect service to check for any malicious apps on your device. Launch the Play Store, tap on your profile picture, select "Play Protect," and tap on "Scan."
Performance issues and battery drain
Not all types of malware come announced or bombard you with ads — in fact, the good ones stay hidden and operate in the background. In recent years, cryptojacking has climbed up the popularity ladder of cyberattacks, especially on Windows PCs. There have been notable instances of cryptomining malware on Android phones as well. Though these aren't primarily designed to steal your data, they actively use your device's processing prowess to mine cryptocurrency.
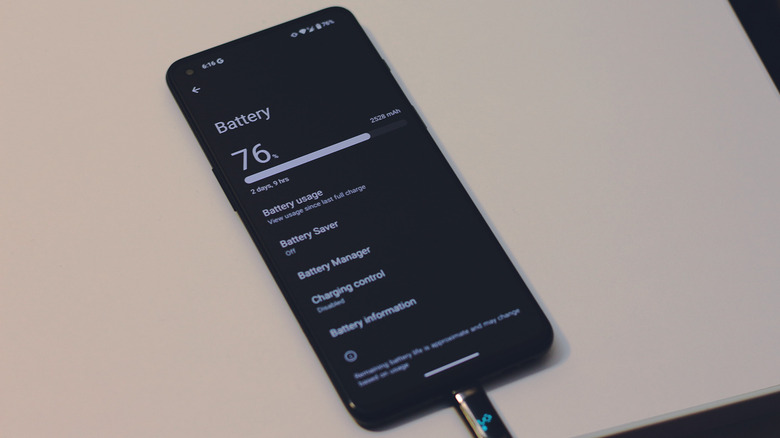
This happens in the background, and a big telltale sign of such malware is sluggish device performance. If you've already closed all of your recent apps and have made sure you don't have any obvious background services running, your phone shouldn't be running slow or overheating. Increased, unexplained battery drain is also a solid indicator that your device may have been infected with malware.
Navigate to Settings > Battery to see app-specific usage. If things don't add up, or you see an unfamiliar app or process name consuming an unnaturally copious amount of battery, it's time to dig deeper. In addition to cryptojacking attacks, spyware and keyloggers also work tirelessly in the background, which may increase battery consumption and contribute to performance issues. Checking for sudden data spikes will also help you determine if your phone has been hacked.
Suspicious messages or login attempts
Phishing remains one of the most successful forms of social engineering attacks. It's often carried out via email or SMS through links to websites that seem legitimate and have you voluntarily enter your credentials. At this stage, your device isn't technically infected with malware — but the presence of mysterious texts or emails puts you at a much greater risk of falling for these attacks.
We've covered how using the SLAM method can effectively safeguard you against phishing attacks. In essence, avoid clicking on links or downloading attachments from sources you don't fully trust. Gmail already does a decent job at filtering out spam emails and protects you from clicking on potentially dangerous links unless you mark the sender as safe.
Spear phishing is when an attacker targets an individual or organization specifically. You might even receive texts from people who claim to know you on a personal level. This makes victims fall for phishing attacks much more easily. Setting up two-factor authentication can prevent unauthorized login attempts, even if you do end up losing your credentials to a phishing attack. Unfortunately, this hasn't stopped attackers from requesting 2FA codes. Many two-factor prompts don't even require the input of a code — some approve sign-in requests when you press "Allow" or "OK." This is why it's important to look out for random authentication requests on your phone and only allow ones that you've requested.
What to do if your phone is hacked
Unexplainable battery drain, mysterious texts, sluggish performance, pop-up advertisements, an infestation of login requests, or unfamiliar apps being installed — these are all signs that your phone has probably been tampered with. Beyond uninstalling suspicious apps and changing your credentials, it's important to thoroughly inspect your device to ensure you don't have any eyes still prying.
iPhones are comparatively more difficult to hack into, given Apple's stance around a tightly-knit ecosystem. It's much easier to sideload apps on Android, and while Play Protect should actively notify you of any threats, you might benefit from using one of the many dedicated Android antivirus apps. These not only look out for installed apps that may be shady, but also scan media, texts, and browser data for malware.
It's much easier to find vulnerability gaps in outdated versions of Android and iOS — which is why you should always keep your phone up to date. To check for updates on Android, navigate to Settings > System > System Update, and on iOS, head to Settings > General > Software Update. If you still suspect that your data may be at risk, a full factory reset is highly recommended. This will get rid of all apps and data from your phone and give you a fresh start.