Alleged Hacker Arrested In Cyberattack That Shut Down Airports - Here's What Happened
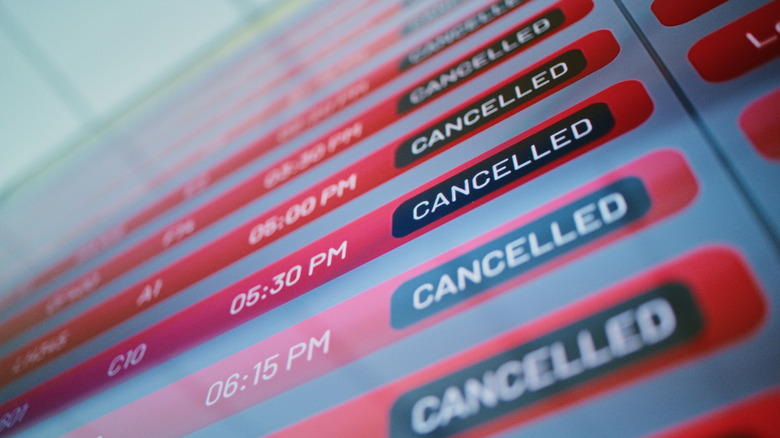
On Friday, September 19, multiple airports around the EU and United Kingdom experienced a string of flight delays and cancellations, all of which were attributed to a cyberattack that occurred that day. The disruption lasted through the subsequent weekend, and while the system was back online by Monday, airports in London, Brussels, Berlin, and Dublin were still experiencing periodic interruptions throughout the week.
On Wednesday, the United Kingdom's National Crime Agency announced that an individual has been arrested as part of its ongoing investigation into the cyberattack. The NCA has not publicly divulged any identifying information about the alleged culprit, only that he is a male in his 40s. The alleged culprit was arrested in West Sussex on Tuesday evening on suspicion of Computer Misuse Act offenses, though he has been released on a conditional bail.
The NCA's investigation into the alleged culprit's means and motives are ongoing, and it has secured cooperation from the companies affected by the hack while they attempt to piece things back together.
A ransomware attack paralyzed systems provided by Collins Aerospace
According to the NCA's investigation, the precise nature of the cyberattack was a ransomware attack that targeted the check-in systems, provided by United States-based aviation company Collins Aerospace, to the affected airports. As a result of the ransomware attack, both airport workers and travelers experienced difficulties, such as boarding passes failing at departure gates. This forced the affected airlines to check passengers in using pens and paper, leading to hundreds of delays and flight cancellations.
Collins Aerospace is still in the process of rebuilding the affected system, with no stated timeline for when it will be completely back to normal. In a statement obtained by the BBC, the company has told airport workers to expect at least another week of manual workarounds. Collins Aerospace's parent company — United States defense contractor RTX, which also manufactures weaponry like Tomahawk Missiles — confirmed the nature of the attack to the U.S. Securities and Exchange Commission. The U.S. company is currently working with the NCA on its investigation.
As part of the NCA's statement on the incident and arrest of the alleged culprit, Deputy Director Paul Foster noted that despite the arrest, the investigation into the overall events of the attack is still in relatively early stages, and remains ongoing.