Passkeys Explained: How They Work, And Why You Should Use Them
A hardware security key, like those offered by Yubico, is often said to be the most secure form of authentication. All the sensitive sign-in credentials are saved on a physical device that is always in your possession. Passwords, on the other hand, are prone to phishing and leaks, among other threats. Over the years, certain companies have embraced biometric authentication as a sign-in protocol across key services.
The key takeaway here is that your login credentials are the safest when they are saved and deployed locally. With that objective in mind, Google joined hands with Apple and the FIDO Alliance to develop a system called "Passkeys." At the fundamental level, passkeys are an alternative to the alphanumeric passwords we are used to: Instead, verifying a person's identity is offloaded to the local authentication method.
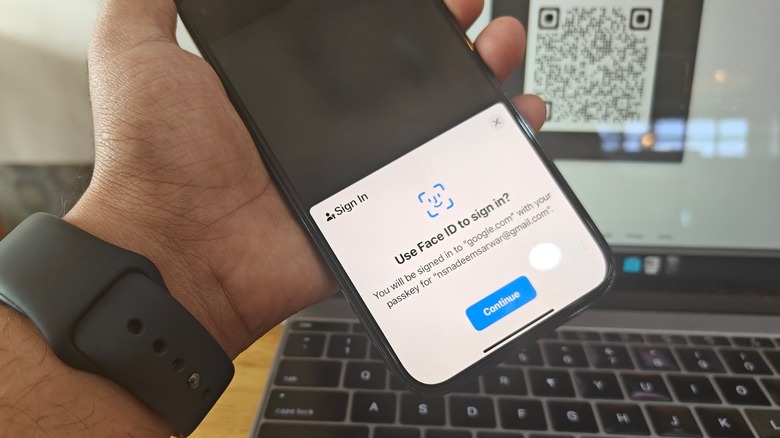
If you are using a fingerprint sensor to unlock your Android phone, the same can be used to log in to your Google account across the web. In the case of Apple devices, it could be Face ID or Touch ID that does the job. If you have a local PIN, pattern, or password set up to unlock your phone tablet, phone, or computer, that is what will grant you access to your accounts.
Technical foundations of passkeys
The idea is here that no one, except the owner of a device and the services running on it, should be able to access them. In doing so, you are protected from advanced forms of attacks such as one-time code interception or any other intermediary step linked to your preferred two-step authentication measure.
At the most basic level, passkeys can be classified as digital credentials that are tied to a user account and the website, without any middleman access and direct link to the device in your hand.
The foundation system for passkeys is the Web Authentication (Web Authn) standard, which relies on a public cryptography pipeline. For the unaware, cryptography refers to the process of converting sensitive data into a noun-decipherable format so that even if a bad actor gets access to it, they won't be able to use it anywhere. The cryptographic data is protected using a decryption key, which is located on-device so that only the intended user can recover the original data.
When you set up passkeys, the operating system powering your device will generate a cryptographic key pair locally, which is unique for each device. One of the keys is stored on a server, but this isn't required for sign-in. It's the second copy stored on your device that is exclusively used to sign in for services. Ultimately, no one, except the owner of a device and the services running on it, should be able to access them.
Why passkeys are a safer option?
The most obvious functional benefit of passkeys is that you no longer have to remember an alphanumeric potpourri as your password. Instead, you rely on a far more secure method of authentication that you don't have to remember, nor can it be spoofed. Depending on the device in your hand, users authenticate their identity using a biometric medium like a face or fingerprint scan.
There are a few reasons why should use passkeys. Since passkeys are not composed of text, numbers, or symbols — not even the most advanced machines that currently exist can brute-force past the authentication wall without physical access to the device. Once enabled, passkeys are not held back by platform or operating system limitations, and there is no distinction between the sign-in pipeline followed by an app or website.
The process of passkey generation involves two keys — one that is shared with a website (or app) where you want to log in, while the other is always stored locally on your device. This scattered approach makes a match handshake mandatory, meaning a fraudulent website or application masquerading as a genuine service can't ever trick a passkey-protected chain.
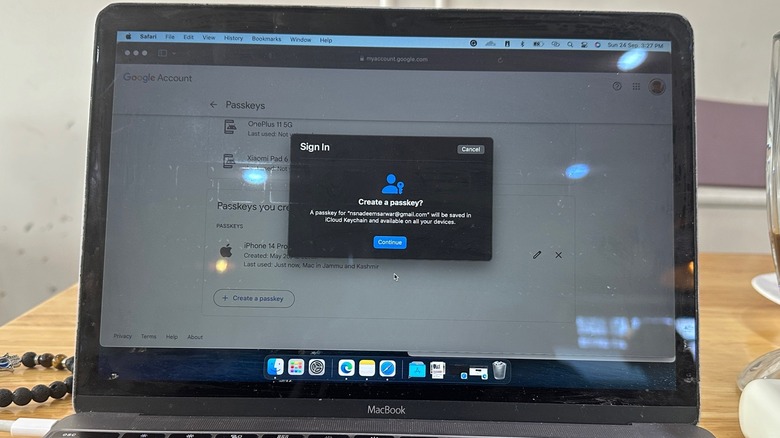
Finally, the versatility and ease of use makes passkeys easy. Google's Password Manager and Apple's iCloud Keychain support passkeys, which means you are covered across both the phone and PC segment.
Passkeys are where convenience is at
When you try to verify your identity on any platform, you will see multiple options like scanning a QR code with your phone, inserting a physical security key, using the passkey stored on your PC, or simply unlocking a trusted phone. Passkeys are not just safer, but far more convenient.
Instead of waiting for a two-step verification check, which can be finicky for multiple reasons, all you need is a biometric scan or screen lock on your phone when the verification prompt appears. Passkeys are cross-platform, which means you can authenticate on macOS using an Android phone. Plus, they are synced, depending on whether your devices are tied to Google Password Manager or Apple's iCloud Keychain.
Even if your laptop doesn't have a passkey setup, you just bring your phone close to it and verify your identity with the preferred screen lock method. Passkeys are also dramatically faster (more than 2x in some cases), and offer the least amount of friction by taking multiple-factor authentication out of the equation.
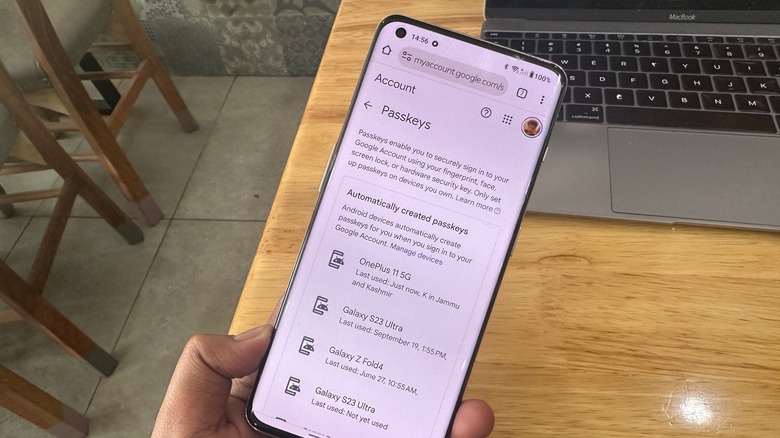
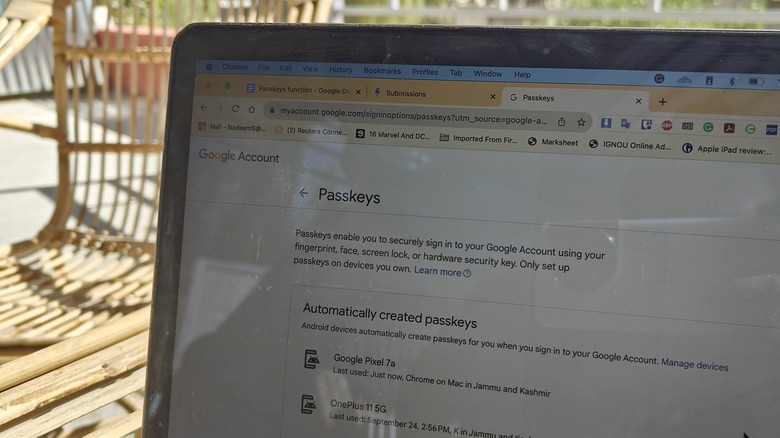
Google automatically creates and saves passkeys for your Android phone, so there's that flexibility, as well. There is no need for re-enrollment when you switch to a new device tied to the same account. You also don't have to wait for 2FA SMS codes, which may incur additional charges if you are in a roaming zone, nor do you have to worry about cellular network coverage.