How Android 16 Will Detect Fake Cell Towers To Help Keep You Safe
Upcoming Android devices running Android 16 will soon help users protect themselves from IMSI-catchers, colloquially known as Stingrays. These devices pretend to be legitimate cell towers and trick nearby cell phones into connecting to them, at which point they can track the phone's location and potentially intercept communications. Some Stingrays can even install malware. They are deployed for a variety of reasons, including criminal investigations; in at least one case, the FBI withdrew armed robbery charges rather than reveal how it had located the defendants. However, Stingrays are increasingly suspected of being used to spy on lawful protestors and political dissidents, although it's unclear how commonly Stingrays are used for those purposes.
Though originally designed for military use behind enemy lines in Iraq and Afghanistan, Stingrays predictably made their way home and are now deployed against United States citizens. American law enforcement began acquiring these tools during the mid-2000s, with the Los Angeles Police Department reportedly using them as early as 2006. Today, they are widely used by police across the United States, as well as by the FBI, DEA, NSA, and DHS agencies, including ICE. They have proliferated to countries including Canada, the United Kingdom, Ireland, and Saudi Arabia. There has also been one documented case of French criminals using a Stingray as part of a phishing scam.
However, smartphones are finally developing defense layers against these privacy threats, with a major safety feature now out for supported devices running Android 16. By smartly analyzing your network, the next crop of Android phones will be able to detect fake cell towers and warn you of them.
Android will warn users about Stingrays and similar devices
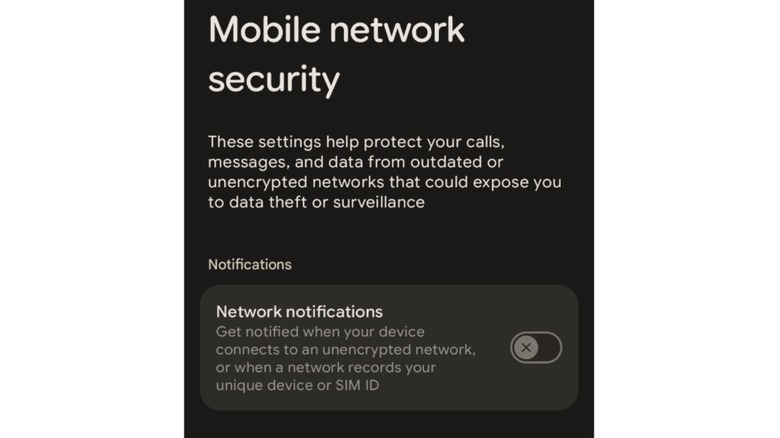
Although it's difficult to prevent your smartphone from connecting to a Stingray outright, Google is doing the next best thing. A new feature in Android 16 warns users when their phone connects to an unencrypted network, or when a network requests their device's identifying information. The feature, called Network Notifications, can be found in a new Mobile Network Security page in the OS settings. It sits alongside an older feature that prevents devices from connecting to a less secure 2G network.
2G network protection was already included in Android's Advanced Protection suite, which you should enable if you're concerned about this sort of thing. A Stingray will often knock your phone down to 2G to make it easier to intercept traffic. 2G networks are mostly defunct in the U.S. and some other countries, so there's almost no reason to leave 2G enabled on your device.
Unfortunately, your current Android phone probably doesn't support network notifications and never will, at least if you're reading this in 2025. The setting is only supported on devices with modems that support IRadio 3.0. That rules out all mainstream Android devices except for the recently-launched Google Pixel 10, which runs on Google's latest Tensor G5 SoC. However, we expect to see this feature widely available on devices launching with the next generation of processors from Qualcomm and MediaTek. Here's hoping Apple follows suit, since the newly launched iPhone 17 lineup does not appear to have a similar trick up its sleeve.
What to do if you think your phone is connected to a Stingray
Fake cell towers are one of the most unexpected ways your Android phone can be hacked, and the new network notifications feature in Android 16 is not infallible. It can only tell you when your network is unencrypted, or when it requests certain device and SIM information. However, some legitimate networks exhibit similar behavior, with the feature merely letting users decide how to respond. So, what should you do if you get one of these notifications?
Context is crucial. If your future Android phone informs you of an unencrypted network or device identifier request while at a protest or political event, for example, it's worth treating the threat seriously. The same goes if you are a likely target for surveillance, such as an activist, journalist, influencer, or whistleblower. The first thing you should do when you suspect a Stingray may have hijacked your phone's cellular connection is turn off your Android phone or switch to airplane mode. Make sure all wireless radios are disabled, including Wi-Fi, Bluetooth, mobile data, and GPS. Do not reconnect to your mobile network until you are reasonably far away from your initial location.
You can also make your communications more difficult to intercept by using an encrypted private messaging app such as Signal or even WhatsApp, as cell site simulators cannot read end-to-end encrypted messages. Moreover, turning off 2G as described above will prevent most Stingrays from intercepting your communications. You can also look into projects such as Rayhunter, a tool that runs on mobile hotspot devices and scans for potential Stingrays.