Your USB Cable Or Device Could Be Hiding Malicious Hardware: Here's How To Stay Safe
Most people would never suspect that something as simple as a USB cable could be a threat. After all, the humble USB cable is merely a conduit between devices, about as unthreatening as a piece of tech could be. But that simple facade may be hiding a lot more than you bargained for. Not all USB-C cables are the same. The smaller tech gets, the more places there are to hide wireless radios, extra microchips, and more. Cables and small gadgets of all kinds are new frontiers for hackers, government intelligence agencies, and other entities.
In recent years, and the past decade especially, there have been numerous reports of not just cables but phones, pagers, servers, and more hardware devices hiding everything from microchips to explosives. While these attacks are mostly carried out by state-affiliated actors, and are usually directed at corresponding targets, it's important to be aware of what's possible with modern hardware. So, in this article, we'll break down just a few of the disturbing implants that have been discovered in seemingly normal gadgets and cables.
USB cables can contain a lot more than you'd think
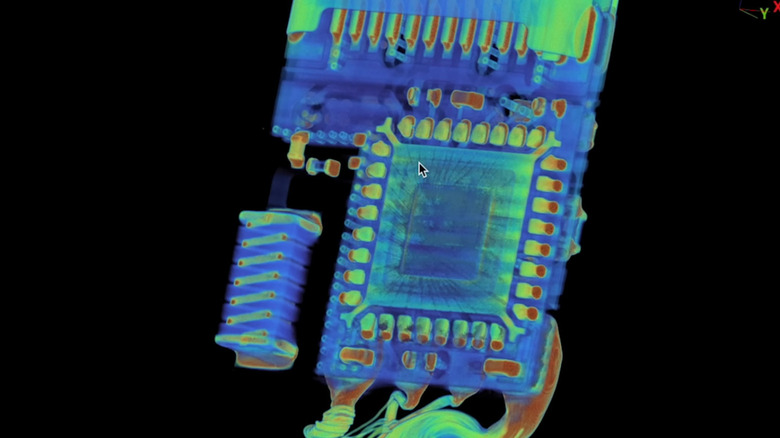
You've probably never thought about 3D scanning your USB cables. However, short of cutting them open and destroying them, that might be the best way to discover malicious hardware hiding within them. Researchers were able to confirm that it's possible to add a hardware payload into a USB cable that won't be noticed unless examined with a three-dimensional scan.
The cable in question was the O.MG USB-C cable. When manufacturing solutions firm Lumafield subjected the O.MG cable to a CT scan, they found a radio antenna, a microcontroller, and a secondary circuit die. These tools are used to inject payloads onto devices, including keystrokes and mouse movements, as well as to conduct keylogging and geo-fencing attacks, among other chilling applications. Before you start to panic, it's worth noting that this cable wasn't trying to pass itself off as innocuous. It is a specialized tool for Red team scenarios that costs $120 or more at press time and is marketed for teaching and field research purposes. With that said, if someone wanted to pass it off to you as a normal USB cable, you'd be unlikely to notice.
To be clear, you don't need to start sending every cable you buy to a lab. As long as you're buying a good brand of cable from a reputable seller, your odds of getting a cable that's been tampered with are exceedingly slim. Fitting extra components into a cable requires money and expertise, resources that likely won't be expended to attack a random person. If you want to take precautions, the maker of O.MG cable also sells a malicious cable detector that lights up if anything unusual is detected.
Devices from pagers to servers have been tinkered with by malicious entities
Your phone or other device can also contain a malicious payload, and there have been multiple examples in the past few years of hardware being secretly intercepted for disturbing purposes. The most recent incident to make headlines was an Israeli intelligence operation in September of 2024 that killed dozens, according to The New York Times. Israeli operatives had set up a front company to manufacture hundreds of pagers and walkie-talkies containing remotely triggered explosive devices. Those tampered communicators were distributed throughout Lebanon and Syria to people whom Israel suspected of being affiliated with the militant group Hezbollah. The attack was triggered in two stages. First, the pagers rang, prompting users to put the devices near their faces to answer the supposed call. This ensured that the explosion triggered shortly after would cause the most lethal damage. 32 people were killed, including a nine-year-old girl who answered her father's pager. Thousands more were injured.
Most people likely have no reason to fear a similarly violent attack. Espionage is far more likely. In October 2018, Bloomberg reported that China had installed microchips slightly larger than a grain of rice in servers from Super Micro. Alarm bells went off across the United States, since the company's servers were used by Apple, Amazon, and the Department of Defense, among others. However, Apple and Amazon blasted Bloomberg for the report, demanding a retraction, and Super Micro later released an independent audit which found no such spyware. For its part, China's own intelligence agencies have uncovered spy devices disguised as USB flash drives and other gadgets, as reported by Chinese state media affiliate Global Times in August 2024, and at least one Chinese handset with potential malware has raised concern.