Protect Your Privacy: Here's How To Do It Now
Facebook may be getting a lot of long-overdue chastisement over its business practices but guess what? It's not the the only one. It's just the latest company that happened to get caught red-handed doing bad things. From Google to Twitter to, yes, even Apple, these companies will always take a piece of your private data, often with your unknowing approval. But while they are both legally and morally obligated to protect your privacy, you cannot wait for them to clean up their act. Nor can you expect them to. At the end of the day, you are your own first line of defense. Here's how you can put up your privacy wall or at least make sure very little gets out without your knowledge.
Assume the worst
You know those scary, paranoid people always yelling that "they" are out to get you? Turns out they're right. Very few companies offer free services without asking for anything in return. Especially for-profit, publicly traded ones. And whether you pay for the service or not, they will always ask you to give up something in return, usually a piece of your information, often in the guise of improving service.
All software and services have terms or licenses you have to agree to before using them. These are presented to users, often during setup, simply because the law requires it. These documents, however, are never meant for the layperson to understand. To put it in another way, they're like lawyers talking to other lawyers. They're worded in often convoluted ways to make sure that the owner's legal bases are covered in case, you know, you discover later on that you actually agreed to send them your address book.
That's why almost no one bothers to read these EULAs and ToS. Which is a legally dangerous habit, of course. They can't be expected to understand them fully anyway. That is why there are now sites and services that try to distill these legal mazes into their core essences. But how do you expect to find time to read even those?
So here's a shortcut: already expect that you're signing away a part of your privacy when you (falsely) claim you've read the terms of services. Often, what you're sharing is pretty obvious from the service you're signing up for. Gmail will have your contacts and email, Twitter will have your tweets and media, etc. They will all claim to take good care of your data and make sure they're anonymous. You can never really be sure. But if you're still willing to go forward, then read on.
Permission not granted
There's a geeky principle in computer science called the principle of least privilege. It simply means that you give something, like a program or a user, just enough access or privileges to do what it needs to do and nothing more. Alice doesn't need to have access to Bob's user account (unless Alice was the system administrator). Your media player has no businesses changing system settings, and your text editor definitely doesn't need to upload your contacts and calendars to some remote server.
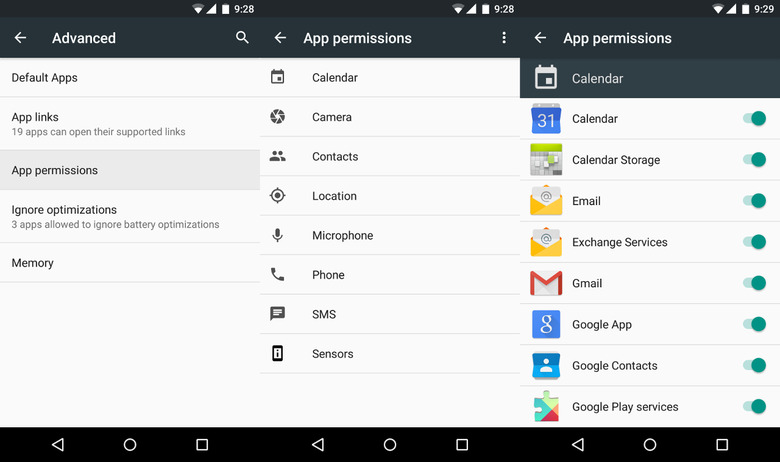
Despite being written by those with computer science background, most apps and services are designed to be the opposite. They grant or ask blanket permission for almost anything and everything and then expect users to work backward to revoke those permissions.
It used to be harder, admittedly. In the past, especially on Android, you couldn't even revoke those permissions piecemeal. It's an all or nothing situation that has fortunately been made obsolete by newer Android versions (unless you're still on now-ancient Lollipop). So those apps you have installed on your Android or iPhone? you can pretty much cherry pick what you want them to be able to access. A word of caution, though. App developers still haven't upgraded their mentality to this new system and apps may crash at times. Fortunately, it's as easy as flicking a switch, though it sure could be easier.
This is admittedly harder to do when it comes to web services, many of which don't have an equivalent feature. Web browsers, on the other hand, do have such permission switches, albeit limited to what they can access on your computer. Sadly, it almost takes a computer scientist to figure out where those settings are or how turn them off.
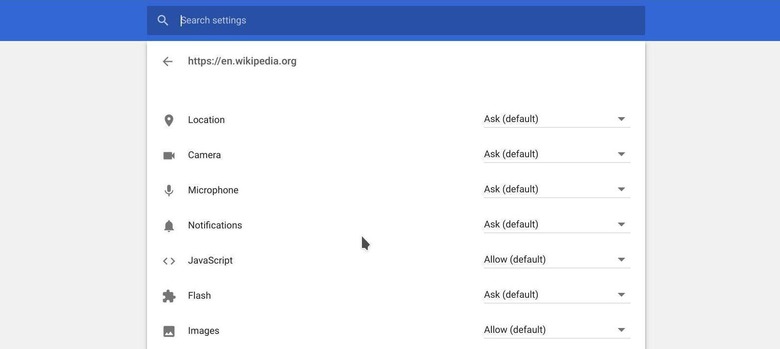
Spring cleaning
Services like Facebook and Google have become so big that you use them for things beyond, well, Facebook and Google. You can use them for single sign-on (SSO) or login convenience. Some mobile games will even use them to associate account data so that you can switch to any device and have your in-game data move with you. And, of course, some will gladly post your latest achievements for you, and reward you with in-game shinies for letting the world know you're playing their game.
It is, however, also a point of security and privacy failure. More often than not, users simply allow games and apps access to their social account, which sometimes gives them more than necessary permission to access your data. These games and services could also disappear or change ownership, and the new owners might be less conscientious about respecting their customers' presumed right to privacy.
The latest Facebook scandal has many shouting #DeleteFacebook. For some, that's nearly impossible. What's not impossible, however, is to do a sweep of Facebook's, and Google's, and Twitter's, settings and connected apps to ensure no holes are left open. Unfortunately, you can't expect them to do it for you. Especially not if they can profit from it.
Share the work, share the blame
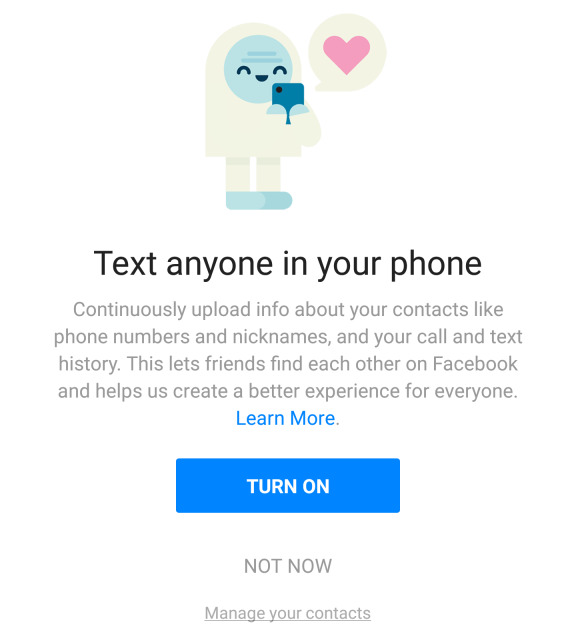
Now, this is admittedly a tricky one. The Internet has made the world such a smaller place and connected so many people together that we have, in part, also become somewhat responsible for other's privacy as well. How? Because that address book, phone number, or email address you give Facebook and friends access to also contains your friends' contact information. So it's not really just your information you are sharing with them. You are also sharing your friends' information and, chances are, they never agreed to that.
It's probably still a legally grey area in many jurisdictions and companies will always say that you gave them the permission. Whether that permission also covers your friends and contacts is something lawyers and judges will have to squabble over, but be sure you are aware of that fact. And make sure your friends are as well.
Think before you click
Good user interfaces are designed to guide users towards a specific direction. Some user interfaces are too good at doing that, guiding users to click or tap on an action with little thought about the consequences. There's a reason why some "Skip" or "Not Now" buttons are hidden in corners or less emphasized.
Windows installation wizards have also ruined us forever. We click and tap "Next" with wanton disregard for what was on the screen. Most people would pause and even read paper contracts before signing them. While significantly simplistic, most of the things you agree to in installers and setup wizards are sometimes similar. And are just as legally binding as well.
Wrap-up: update our brains
Much of the above is what some would consider common sense, but history and news have proven how it's the least common sense. We have also grown so accustomed in our ways that it takes a scandal of Facebook-proportions before we even stop to consider what's happening. It is almost ironic that we regularly update our phones and, soon, our homes to the latest technologies but our minds and behaviors are still firmly rooted in pre-Facebook days. And even more ironically, Facebook even profited from that as well.
