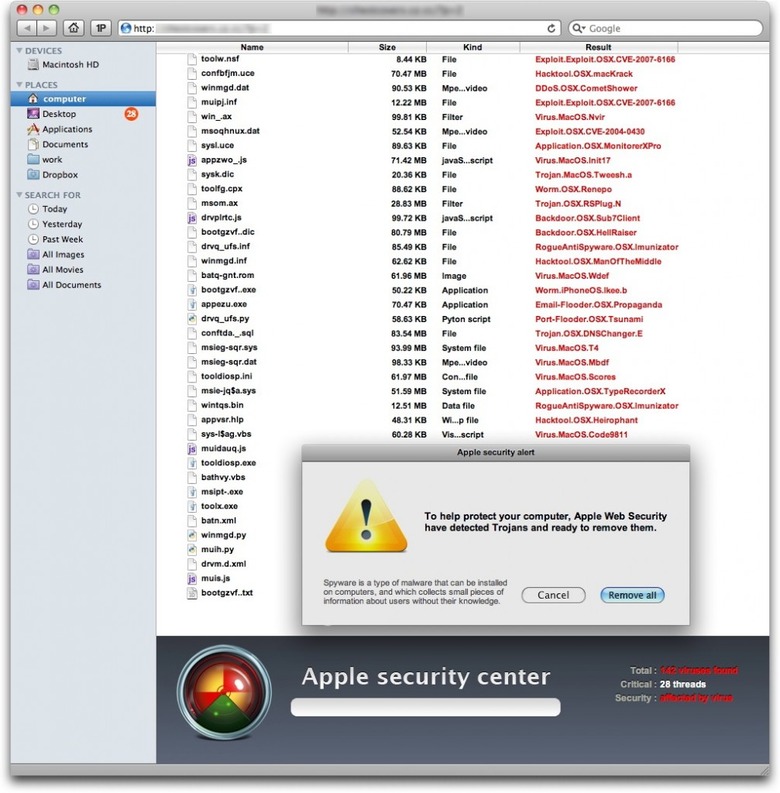
MacDefender Malware Renamed MacGuard, Bypasses Apple Fix
Apple's attempts to handle the MacDefender malware have already been circumnavigated by the apps author, with a new version resilient to the official removal method in the wild within 12 hours. Spotted by Intego, the updated variant now uses a two-part approach to infection. Renamed as MacGuard, it first installs a downloader – with no administrator password required, as long as the person using the Mac has an administrator account - and then that grabs the new version of MacDefender and installs that without the user realizing.
As before, the initial downloader finds its way onto unsuspecting Mac users' machines via specially crafted sites that attempt to score high-ranking Google results through sneaky SEO. The "avSetup.pkg" package automatically begins downloading and, if Safari is set to automatically open files OS X considers "safe" after they're on the Mac, the installer will load without any user-clicking required. It's also set to auto-delete once its work is done.
"Means of protection: the first thing to do is make sure that when seeing a web page that looks like a Finder window, and purports to be scanning your Mac, you know that this is bogus. Leave the page, and quit your web browser. If anything has downloaded, and the Installer application has opened, quit it right away; look in your Downloads folder for the file, then delete it. Next, users should uncheck the "Open 'safe' files after downloading" option in Safari's General preferences." Intego
We're expecting Apple to update its instructions to accommodate this new version, and the company has also promised a software fix that will lend OS X some extra protection. However, until users learn not to necessarily click everything that pops up and/or type in their password without compunction, malware will be out there to take advantage of them.
[via ZDNet]