"GODLESS" Android Malware Threatens 90% Of Devices
Malware isn't something new to smartphone operating systems, especially Android. Sometimes, it's even a point of criticism for Google's platform. There are, however, few exploits, like Stagefright and Heartbleed, that has users, developers, and security researchers scrambling. The new "GODLESS" family of malware, reported by software security firm Trend Micro, seems to be bent on becoming one of those, secretly rooting infected devices and opening them up to further compromise, which is practically any device running Android 5.1 Lollipop or older.
GODLESS actually uses already existing exploit tools so it isn't completely new. Its methods and aggressiveness, however, make it noteworthy. In the bad sense, of course. It doesn't rely on a single exploit but uses multiple ones to get the job done. While some of those exploits are known to already be deprecated, some, like the Towelroot and PinPongRoot exploits, remain unpatched on certain Android versions.
GODLESS is also cunning in the way it takes hold of a smartphone. It waits until the user turns of the screen's device so that it can proceed without showing any visible signs. It uses those exploits to root the device without the user's knowledge or consent. Once that's done, the sky's the limit for the malware user. In most cases, it contacts a remote server to install more apps and malware behind the user's back. Worst case scenario, it could even start spying on the user and pilfering sensitive personal information.
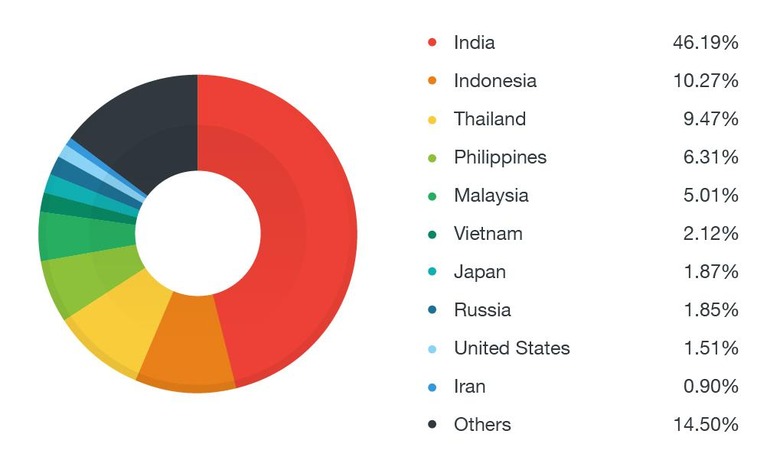
In the past, malware using the same tools that GODLESS uses ships with the file for exploiting the device's security. GODLESS, however, downloads the payload from a remote server and itself doesn't contain the files. That allows infected apps to bypass the Google Play Store's automatic malware detection. Although already destructive by nature, GODLESS' severity worsens with its reach. The exploits it uses have only been plugged up in Android 6.0 Marshmallow. As of June 6 this year, only 10.1% of devices in the market use that version, leaving 90% vulnerable. In Trend Micro's survey, the malware family wreaks its havoc most in Asia, particularly in India.
GODLESS infected apps find their home outside of official Android app stores, though in one case it might indirectly affect even legit clean Google Play Store apps. Some infected apps are able to use the same developer certificate as the clean app, which users might use to install or update over the clean ones. It is therefore highly recommended to install apps, or even them, only from certified and trusted sources. But even then, care should be taken when installing unfamiliar utility apps that might very well be infected.
SOURCE: Trend Micro
