Fox-IT, FireEye DecryptCryptoLocker Saves Ransomware Victims
At the height of the CryptoLocker ransomware plague, security companies Fox-IT and FireEye have teamed up to offer unwitting victims a way out of their predicament without paying any ransom. With DecryptCryptoLocker, these users can send a sample encrypted file and receive a private decryption key, as well a program that can then decrypt all of their affected files. All for free!
CryptoLocker is one of the latest popular forms of malware that have recently taken hold of many devices. Not just personal computers or laptops but even mobile devices as well. The US Department of Justice reported that its recent multi-national effort was able to neutralize CryptoLocker, but apparently it hasn't completely eradicated it. Various strains of the ransomware, malware designed to encrypt files and demand payment for the decryption key, have sprung up left and right to lure unsuspecting victims.
The latest high-profile case is that of Synology's NAS storage whose users have reported being infected by a new CryptoLocker strain ingeniously called SynoLocker. There are many methods that malware perpetrators can use to infect other computers. In Synology's case, SynoLocker gains access via a security exploit in the Disk Station Manager OS running on the NAS. That exploit, however, has been patched since December and infected servers are most likely running older and vulnerable versions. Synology warned uninfected users to make sure they are well up to date, as Synology does not have any means to decrypt those infected files. Lucky break for Synology owners, now someone does.
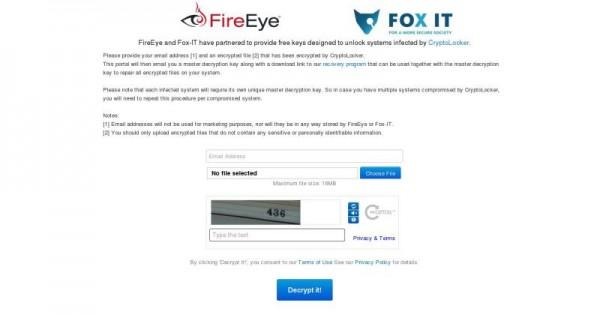
Fox-IT's and FireEye's cleverly named DecryptCryptoLocker tool claims to be able to decrypt those infected files. All that users need to do is to send them a file, via the DecryptCryptoLocker homepage, that has been encrypted by said ransomware. Users should make sure that the file they send doesn't have any identifiable or sensitive information. This is because, their tool will try to decrypt that file in order to find out the master key that can be used to decrypt the rest of the infected system. And they also need the user's email address to send that master key and a link to download the program. It won't be used to add those users to some marketing mailing list, or so they claim.
The tool is being given for free, no (explicit) strings attached, which is a very generous and timely offer which could be a vehicle for both companies to advertise their security prowess. That said, some users might find themselves thinking twice about such an offer, even from a reputable-sounding company, considering it might have been their careless web browsing and downloading practices that have led to the infection in the first place.
SOURCE: Fox-IT