Synology Gets Infected With SynoLcker Ransomware Strain
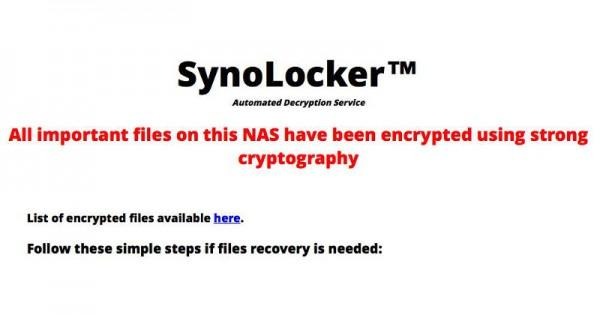
Synology's NAS drives are really getting popular. You can gauge that by the fact that it now has its own specific Cryptolocker strain. This ransomware encrypts data on the user's drive with a key that only the perpetrator knows, who then tries to extort money from the poor unsuspecting user in exchange for getting access to his or her own files.
Yesterday, several Synology users, owners and clients alike, have reported being unable to access their files from their personal servers. Logging into the server revealed the ominous message, basically an extortion in disguise of an encryption service supposedly designed to safeguard random people's data by encrypting that data without their knowledge for free and then asking a fee to decrypt them.
This SynoLocker is noted to be a variant of Cryptolocker, a notorious ransomware that has been making rounds over the Internet. It has produced numerous strains that have infected thousands of computer users. Some have even shelled out money just to get control of their data back, with mixed success. Last June, it was reported that Dropbox has become a favorite vehicle for some of these malware.
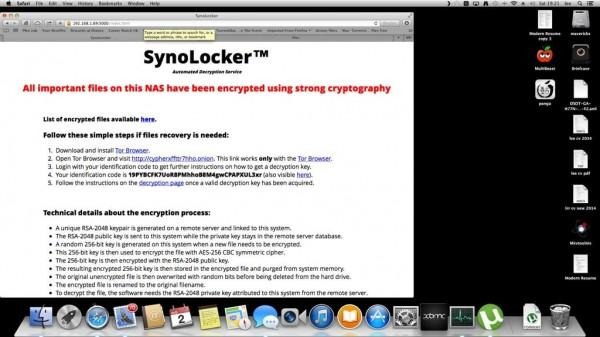
This isn't the first time that Synology's NAS servers have been exposed to malware, but this is probably one of the few times when users' data have been damaged in any way. In June, it was discovered that several NAS drives have been infected by a malware that turns infected servers into a distributed Dogecoin mining farm. The malware would utilize the server's processing resources but generally left files intact and unaffected. SynoLocker, however, targets those files directly in order to have the most amount of damage and extort the most money.
In both malware cases, the perpetrators are able to gain unauthorized access to the NAS via security exploits on the Disk Station Manager OS running on the machines. Synology is usually quick to plug those holes, but in some cases, affected users have not yet updated to the latest security patches. These incidents should serve as a reminder to users to always update to the latest security fixes from manufacturers, especially when it comes to hardware that are known to house many crucial and important data.
VIA: Synology Forums, @Mike Evangelist (1), (2)