Sparkle App Updater Exposes Many Mac Apps To Hacking
In the age before app stores, at least on Windows PCs and Macs, people got their software directly from vendors or third party download sites. App markets, however, gave birth to the idea of a single canonical repository where people can get not only their apps but also updates for said apps. However, not every single software on the planet has jumped aboard, even on Macs. Now those developers and users maybe be given a stronger reason to do so, thanks to a gaping security hole in the Sparkle update framework recently discovered.
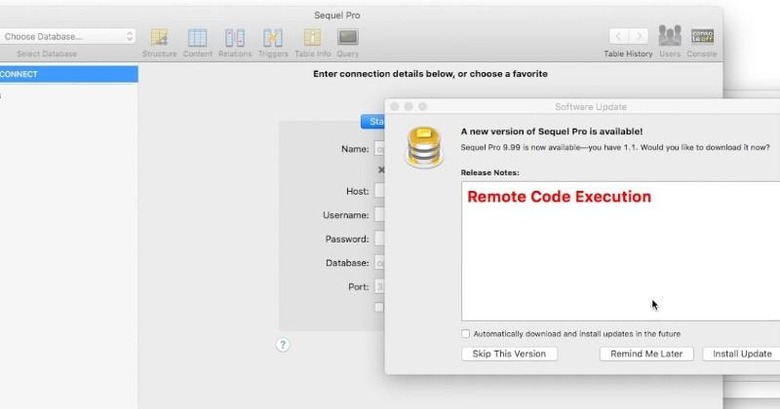
Sparkle is a popular third party framework that many developers, like the famed VLC media player, use to provide a feature usually found in app stores. It allows developers to push out updates easily so that users will always be on the latest and greatest version at any time. While convenient, not being an official framework on Apple's Mac platform does bring its risks, as evidenced by this vulnerability.
The exploit was discovered by security researcher "Radek" in just over a weekend's worth of work focusing on update strategies for Mac apps. He discovered actually two vulnerabilities. The first one is the use of plain HTTP instead of encrypted HTTPS when connecting the user's Mac to the software vendor's server, making it susceptible to a Man in the Middle or MitM attack that could compromise the user's security.
The second vulnerability is related to the way Sparkle uses the WebVIew component in WebKit. It allows for the execution of potentially devious Javascript code and, if the host server mistakenly allows for modifying certain XML files, could also lead to affecting every user targeted by the updater. In this case, the hacker won't even need to make an MitM attack.
There are some good news to this troubling story. Not all apps using the Sparkle framework are affected by the vulnerability. Sadly, some of the more famous software on Macs are actually part of the affected set, including VLC, Adium, Coda, and iTerm. That said, Sparkle developers have already fixed things on their end, which means it is up to the software developers to update to the latest version of the framework in their apps.
The vulnerability affects Sparkle on both OS X 10.10 Yosemite and OS X 10.11 El Capitan. It is, however, important to note that OS X's own app updater isn't affected by either of the vulnerabilities, which could provide incentives for users to get their software only from the App Store, or for developers to start providing their wares from Apple's collection.
SOURCE: Vulnerable Security