Samsung Galaxy Phone Bug Takes Over Phone With An Image Via MMS - Get The Fix Update Now
A vulnerability discovered by Google security researchers was disclosed to Samsung and patched in a software update many modern devices should see OTA this month. This is a required update – as most security-oriented updates are – and it should be loaded by all users of Samsung phones as soon as possible. This update is applicable to all virtually all smartphones sold since the year 2014.
The Samsung connection to the flaw is in the image format Qmage (.qmg), and was discovered earlier this year on Samsung devices. Google's Project Zero bug-hunting team-member Mateusz Jurczyk discovered the bug and reported how it'd potentially affect basically every Samsung device sold in the last half-decade, since Samsung started supporting the Qmage image format in their flavor of Android.
The vulnerability could, potentially, exploit how the Android graphics library (Skia) handles Qumage images. If a Qmage image is sent to a Samsung device, it is (or was) sent to the device's Skia library for processing. If a full-sized image is sent to a phone, the Skia library in Android will process the image in several ways – resizing for potential display in notifications, for example.
How the attack takes place
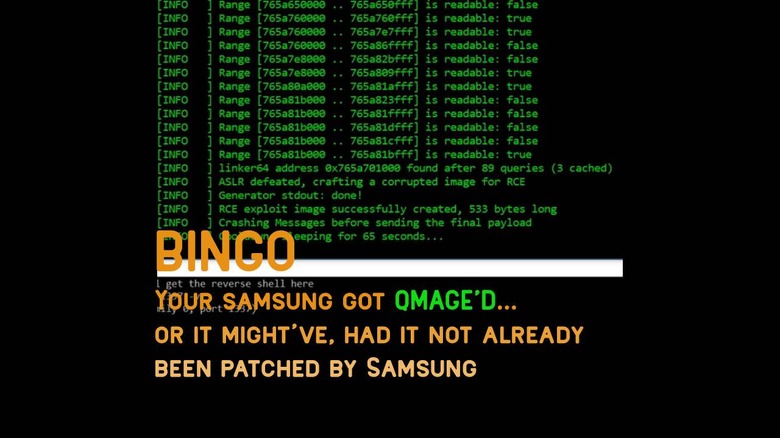
The attacker sends a number of MMS messages to a user of a Samsung device, each MMS message attempting to guess the position of the Skia library in a particular Android device's memory. NOTE: This first step is pretty wild – it requires tens if not hundreds of messages sent over the course of around 100 minutes – it's not very subtle. See the video below to see how it's done.
Once the Android device's Skia library is found (it's randomly place with Android ASLR, which is good, but clearly imperfect as this exploit shows), the next step can take place. The next step includes the Qmage image. This image is sent with the same MMS system as the first hundred or so messages for probing. The Qmage image is encoded in a way that allows the real attack to take place.
All of this can be done without any user input from the victim. Thus, a 0-click vulnerability. It's bad news, of that you can be sure. Luckily, it would appear that the vulnerability was discovered before it was ever utilized to attack a device outside of proof-of-concept work.
Get the fix right now
You'll more than likely have a security update available for you either this week or very, very soon from Samsung if you have a Samsung smartphone. Go to Settings, scroll to the bottom of your list of Settings to find System Updates, tap it, and tap Check for system updates. If you don't already have your device set for automatic security updates, you might also want to take this time to do so.
You'll find more information about the latest Samsung security update in the Samsung Mobile Security Update bulletin right now. This update came in the SMR-MAY-2020 patch.