Samsung Find My Mobile Reported To Be Vulnerable To Attack
One of the biggest objections that detractors of the kill switch have against the theft deterrent measure is that the feature could be used for good or for ill, depending on who holds the power. Those fears might have just materialized with the discovery that Samsung's Find My Mobile feature, which lets users remotely lock or unlock their devices in case of loss or theft, can easily be broken into, giving hackers the power to remotely control access to a victim's Samsung Galaxy smartphone.
Part of the feature set of a kill switch is offering owners, and perhaps law enforces, the ability lock, unlock, locate, and even wipe a smartphone remotely, usually from a web browser. To that extent, Samsung's Find My Mobile is no different, similar in functionality to Google's Android Device Manager and Apple's Find My iPhone. What makes it different, though, is how it was easily exploited to remotely lock a user out of his or her device. The US National Institute of Standards and Technology describes the security flaw in a vulnerability report:
"The Remote Controls feature on Samsung mobile devices does not validate the source of lock-code data received over a network, which makes it easier for remote attackers to cause a denial of service (screen locking with an arbitrary code) by triggering unexpected Find My Mobile network traffic."
The two videos below, which come from Egyptian security researcher Mohamed Baset, show the vulnerability in action.
Just as worrying as the vulnerability itself is the fact that the feature on the smartphone side might be enabled without the user knowing it. Although not enabled by default, once a user creates a Samsung account, which owners might do to get access to Samsung-exclusive apps and services on their device, it becomes enabled. And since users don't know it has been enabled, they might not be aware how to disable it as well.
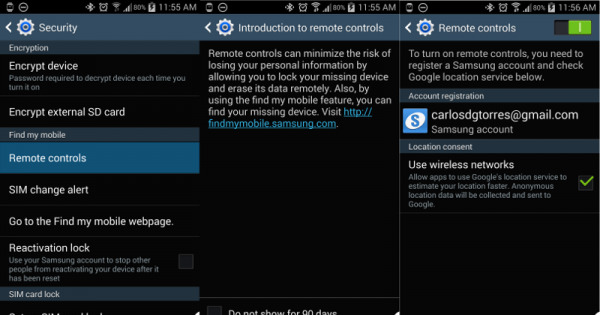
Although it is not representative of similar features on other platforms or devices, it does call into question the "foolproof-ness" of the entire system. Come 2015, California's kill switch bill would practically ensure that similar features be enabled by default without users knowing about it, and consequently without knowing how to turn them off. And if services are as vulnerable as Samsung's, then there is indeed great cause for worry.
SOURCE: NIST
VIA: Computerworld
