Microsoft Reports On Its Superfish Hunting Trip
Lenovo had a fish problem early this year, one that refused to die even when it was ignored. The Superfish adware fiasco left the world's biggest PC maker with mud on its face and an angry mob at its gates. While the scandal has seemingly died out, with Lenovo frantically moving to fix both the technical problems and PR fallout, not everyone is safe yet from the deadly fish. Now it's Microsoft's turn to give its users the weapon of knowledge to better arm themselves. Oh, and they are also providing an updated tool to remove Superfish.
Superfish began innocently enough, as innocent as adware programs can be. It's goal was to earn Lenovo some side profits by injecting ads into users' browsers when looking for certain products. The problem was how Superfish implemented it. It used software from Komodia which, in a nutshell, modified the system's security layers to inject those ads without the user knowing it. And like any other such tool, that same violation of best security practices could be used for criminal activity.
Superfish installs a self-signed certificate on Lenovo computers where it is installed and modifies incoming data by signing it with its own key instead of a trustworthy certificate authority. That key, tragically, works for all Superfish users and can easily be acquired by hackers. This leaves computers that have Superfish installed vulnerable to common Man In the Middle (MITM) attacks. What they presume to be secure connections and programs can actually turn out to be broken and malicious.
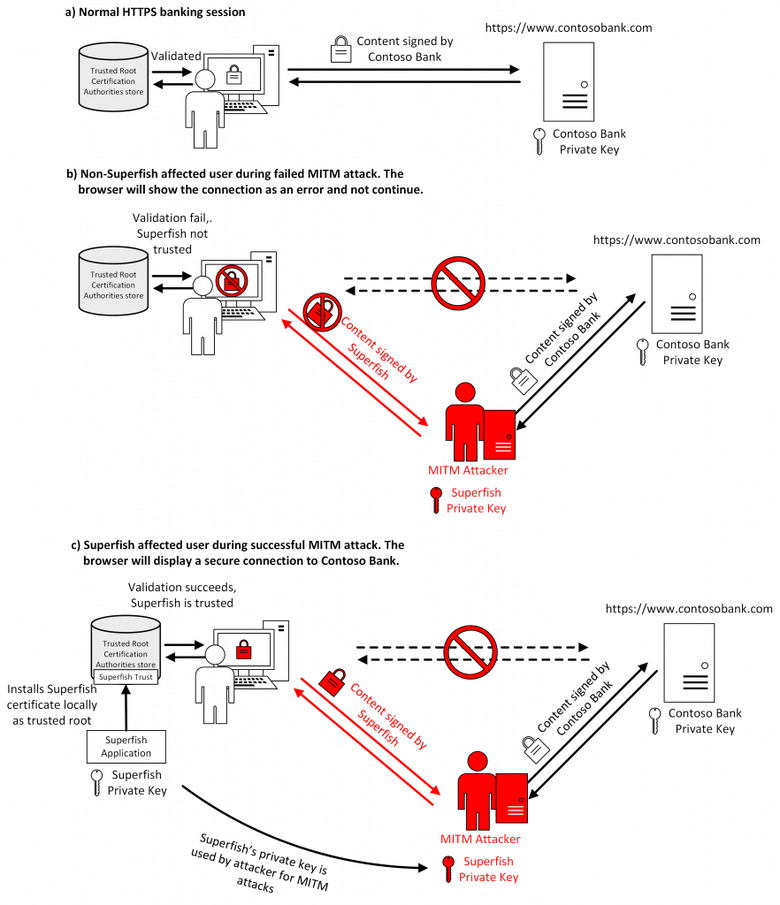
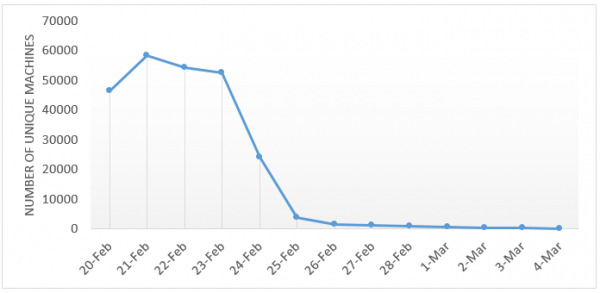
Lenovo at first downplayed the effects of Superfish but later recanted and apologized for their lapse in judgment, both in installing Superfish in the first place and in the way it handled the problem. It worked with partners like Microsoft who updated their tools to detect and drive out the fish from infected Lenovo computers. Microsoft's Removal Tool, for example, adds a new Win32/CompromisedCert family for this very purpose. According to Microsoft's performance report. Superfrish encounters have dropped to zero in just two weeks since it added the malware detection tool.
This is just one of the latest incidents that show users that simple security practices and methods are no longer enough and that even secure lines and technologies like HTTPS and SSL might be vulnerable. The latest FREAK vulnerability, for example, hails all the way back from the 90s and affects many browsers and servers across the US. It didn't leave Microsoft unscathed. Coincidentally, Microsoft has also just available a patch dated March 10 that addresses this very issue.
SOURCE: Microsoft