Flame Cyber-Espionage Discovered In Vast Infection Net
A new and fast spreading malware tipped to already dwarf the notorious Stuxnet has been identified, codenamed Flame and believed to be state-run cyberespionage affecting PCs in Iran and nearby countries. Spotted by Kaspersky Lab, "Worm.Win32.Flame" blends features from backdoor, trojan and worm malware, and once surreptitiously loaded onto a target machine can monitor network traffic, local use, grab screenshots and record audio, sending all that data back to its home servers. Believed to be active from at least March 2010, Flame is tipped to be 20x more prevalent than Stuxnet.
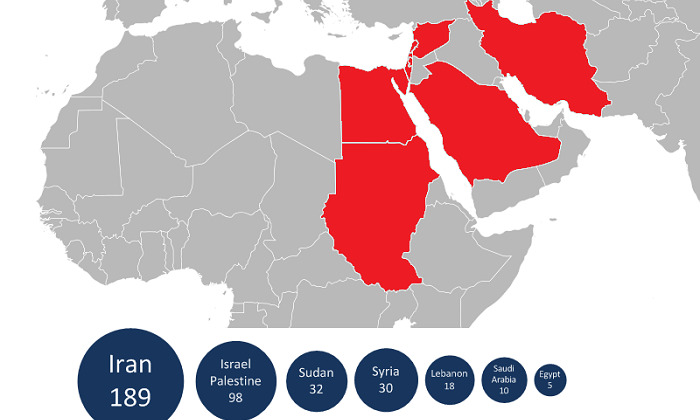
Iran is the most common place Kaspersky have discovered Flame, but it's also been discovered in Israel, Palestine, the Sudan, Syria, Lebanon, Saudi Arabia and Egypt; there are "probably thousands of victims worldwide" the researchers estimate. Interestingly, there's a broad spread of targeted computers, across academia, private companies, specific individuals and others; the operators appear to be cleaning up after themselves, too, only leaving Flame active on the most interesting machines, and deleting it from those with little worth.
Once loaded, Flame has the ability to be updated with new functionality in the form of add-on packages, of which around twenty have been currently identified. The exact purposes of those modules is still being investigated.
What has researchers particularly concerned is the scale of Flame's monitoring abilities. Rather than merely recording VoIP calls, the malware can turn on the PC's microphone and surreptitiously begin its own recordings, for instance, while screenshots are taken when "interesting" apps, such as instant messaging clients, are on-screen. Meanwhile, if the computer has Bluetooth, it can scan for nearby devices and then use the short-range wireless technology to create secret peer-to-peer connections while embedding details on Flame's status in the "discoverable device" information.
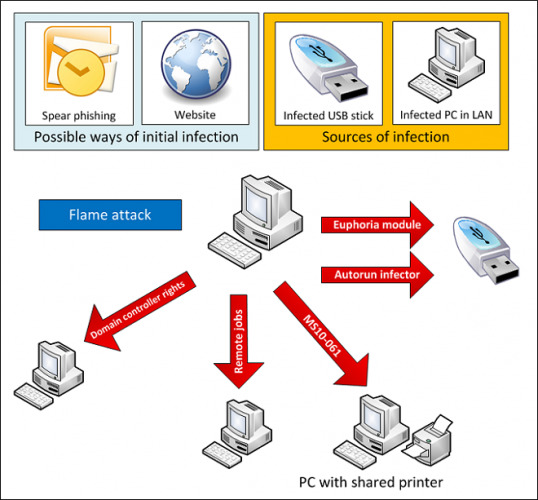
Multiple command & control servers exist, believed to number around 80, and there's still no indication of who, exactly, is responsible either for creating Flame or for operating the servers. Distribution of the malware is believed to be via phishing, compromised sites or direct infection via USB or across a network, but even that isn't completely understood.
"It took us half-a-year to analyze Stuxnet," Alexander Gostev, chief security expert at Kaspersky Lab told Wired. "This is 20-times more complicated. It will take us 10 years to fully understand everything."