eBay Aware Of Vulnerability Allowing Malware Distribution, No Plans To Fix It
A security vulnerability was recently discovered on auction website eBay that allows hackers to embed code on their listings that in turn tricks users into downloading malware. Security researchers from Check Point Software found the loophole back in December, and even contacted eBay to make them aware of the exploit, which takes advantage of the site's rules on hosting JavaScript within listings. Unfortunately the company has said it has no plans to address the vulnerability, as they estimate the use of the exploit to be incredibly rare.
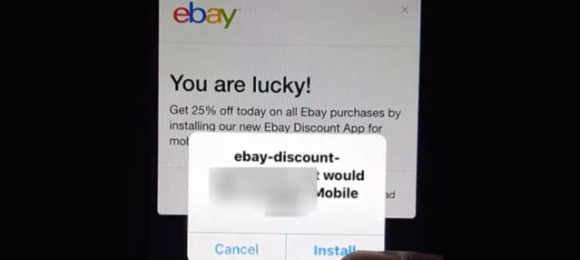
Check Point explained that an attacker using the exploit, known as JSFUCK, is able to get around eBay's restrictions on JavaScript, and embed a code that will pull additional JS from their own server. When a user visits the auction listing, on either a desktop or mobile browser, the code runs and can present them with prompts to download an app, which is in fact malware. An example of the process can be seen in the video below.
eBay has said that it's been in contact with Check Point following their discovery, and while they've improved "various security filters," they don't plan to fix the vulnerability seeing as how it hasn't detected the exploit being used in any fraudulent activity at this point. The company gave ArsTechnica the following statement on the issue:
Since we allow active content on our site it's important to understand that malicious content on our marketplace is extraordinarily uncommon, which we estimate to be less than two listings per million that use active content on the eBay marketplace.
It should go without saying these day, but users need to know that they should never accept prompts to install or download something from a webpage, especially if it's for a third-party app.
VIA ArsTechnica
SOURCE Check Point