Dyre Wolf Malware Transfers Victims To Live Operator
IBM has detailed a new variation of the Dyre malware, which it is calling "The Dyre Wolf". The malware targets large enterprises, and comes with an unexpected twist: a bit of social engineering involving a live operator posing as a representative. When on the phone with this operator, the hackers on the other side use banking information provided by the victim to initiate a large wire transfer...and in some cases use a DDoS attack to keep the company from discovering the transfer until it is too late.
According to IBM, Dyre Wolf has been used to steal in excess of $1 million from companies, and that the weakness is found in the company's own workers, who unknowingly fall for the scam and give away banking information to a live operator. Dyre Wolf, once on an infected machine, waits until a banking website is accessed.
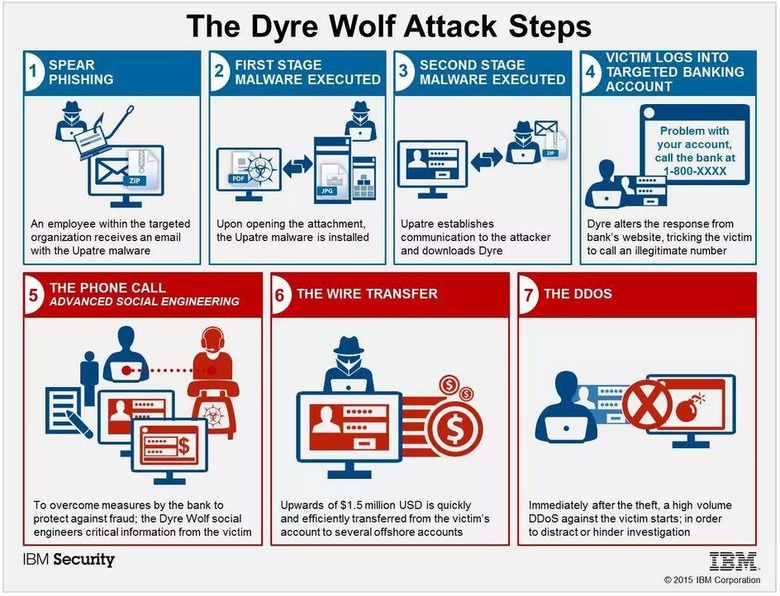
When it is, the malware redirects to a page saying that the site is experiencing technical difficulties, and will provide a phone number the worker is supposed to call for assistance. That number leads to a live operator working for the "experienced and resource-backed cybercrime gang", who knows which bank the victim was trying to access.
The operator then poses as a bank representative and collects information from the victim, initiating a wire transfer while the victim is still on the phone. According to IBM, the transfer is already complete by the time the victim hangs up. The key to solving this issue lies in employee training — companies must ensure their workers are properly trained to spot odd or otherwise suspicious activity and report it.
SOURCE: Security Intelligence
