Arduino-Based KeySweeper Charger Sniffs MS Wireless Keyboards
For geeks and professional typists, the choice of keyboard is like religion and some of them adhere to the religion of Microsoft's Wireless Keyboard line. These users, however, now need to be rather aware, if not paranoid, about their beliefs. Samy Kamkar, a hardware enthusiast and security buff, has just developed an Arduino-powered contraption that can sniff out any and every keystroke done on any Microsoft Wireless Keyboard within range, rendering even the most secure of passwords useless. And it even functions as a real USB wall charger to boot.
To some extent, this is almost unavoidable. Wireless keyboards, naturally broadcast their data over the air to a receiver, which, in itself, is vulnerable to sniffing. The fact that it uses 2.4 GHz signals and even proprietary ones at that will be of no help against the most arduous hackers and reverse engineers, as this inconspicuous spying device reveals.
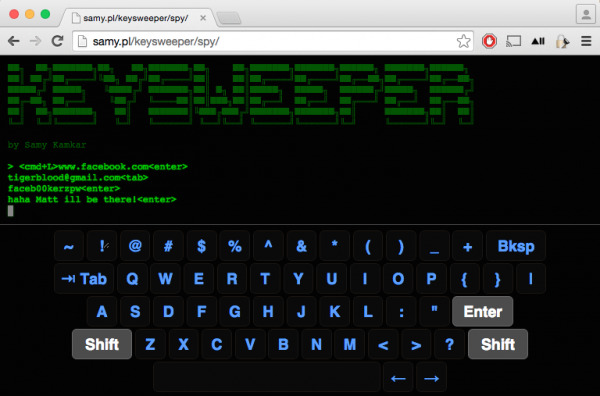
There is perhaps some reprieve in the fact that the KeySweeper isn't exactly easy to make, but it is possible and feasible for makers and modders. All the source code, schematics, and instructions are available on the Internet for everyone to peruse, which unfortunately could include less desirable elements of society.
Aside from sniffing and spying on keystroke, KeySweeper has some other interesting features that will fascinate its makers and users. Of course, there's the fact that it does charge your device, so it can masquerade as a normal, if not ancient looking, USB charger. The LED light that chargers usually employ to indicate power can be subverted to indicate, for example, typing keys. And it has its own battery so that, in the event that the charger gets unplugged, it will continue working for some time until it is plugged back in.

This device is naturally a scary thing for Microsoft Wireless Keyboard users, especially as there doesn't seem to be any immediate safeguard against it short of Microsoft changing its proprietary signals. That said, the one advantage of having all of these information out in the open is that other security researchers and experts can take a closer look and hopefully whip up some countermeasures.
SOURCE: Samy Kamkar
