How Apple Lockdown Mode Could Keep The Worst Spyware Off Your iPhone
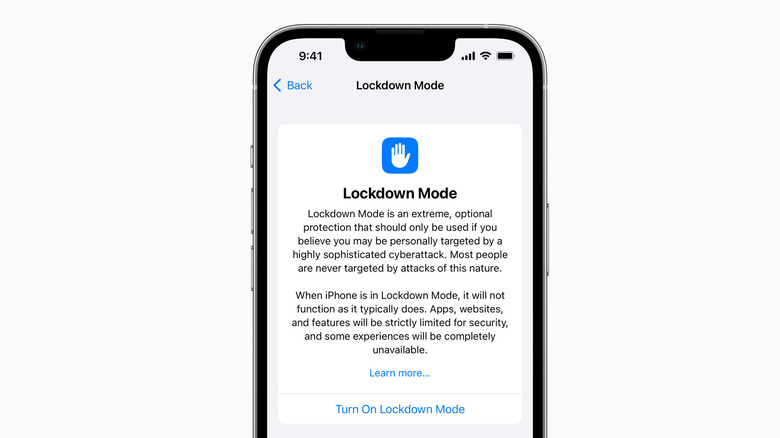
Apple is calling it an "extreme, optional protection" for users such as human rights activists, politicians, and high-ranking government officials, among other people that are at the risk of covert surveillance by having their phones and other personal computing machines hacked. The new safety feature will begin rolling out to the public with iOS 16, iPadOS 16, and macOS Ventura this fall.
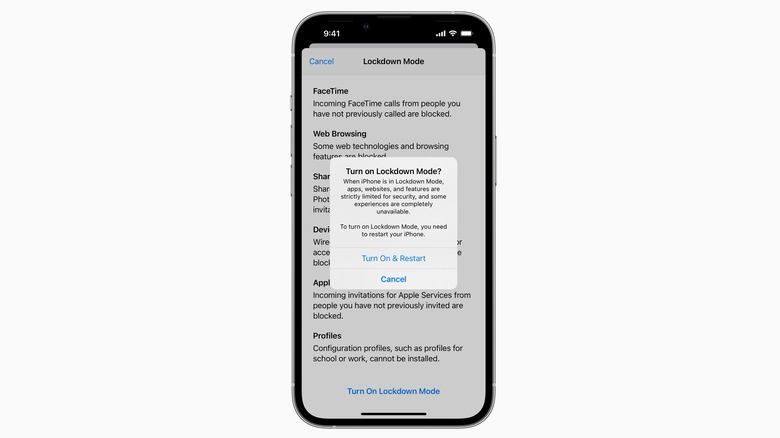
However, Lockdown Mode has already started appearing for users running the third beta of iOS 16 that is now being seeded to eligible iPhones. The core premise of lockdown mode is to shrink the attack surface that is exploited by spyware to do its job. In the past, Israeli firm NSO Group — the creator of the infamous Pegasus spyware — created a zero-click hack that exploited an iMessage vulnerability. By limiting the very feature set of iMessage, Apple aims to shut the doors for such exploits to arrive in the first place. As such, enabling Lockdown Mode will restrict a handful of features.
For example, Link previews are disabled in the Messages app, and all attachments – except for image files – are automatically blocked. FaceTime calls and other communication requests from an unknown number are also blocked, and there is also no scope for installing a configuration profile. In case a bad actor gains physical access to the device, Lockdown Mode will disable all wired connections with an electronic device if the phone or computer is locked, minimizing the chances of an all-out brute force attack.
An indispensable tool for the surveillance age
Apple's press release notes that Lockdown Mode will thwart "highly targeted mercenary spyware" and namedrops NSO Group, a company it sued last year for unaithorized hacking of iPhones with the Pegasus spyware, which used an exploit called FORCEDENTRY. CitizenLab found evidence of this zero-click iMessage exploit and published its findings in October last year. In addition to iPhones, the exploit was also said to be effective against Apple Watch and Mac computers.
Ron Deibert, director of the Citizen Lab, praised Lockdown Mode and expressed that it will "help nurture independent researchers and advocacy organizations holding mercenary spyware vendors accountable." Notably, Apple has added a new tier to its bug bounty program that will award a sum of up to $2 million to cybersecurity experts who find a flaw in Lockdown Mode. That's the highest bug bounty that any company has to offer on the planet, claims Apple.
Even though Lockdown Mode is aimed at folks facing a tangible risk of state-sponsored surveillance, it appears that anyone can enable it. Activating the security feature requires a device restart. However, Pegasus is not the only spyware to have gone past Apple's security firewalls. In February this year, Reuters reported that another Israeli company named QuaDream exploited the same set of vulnerabilities to break into iPhones using zero-click attacks. In fact, according to The New York Times, the FBI actually tested the Pegasus spyware on the U. S. soil for a few years.