5 Immediate Steps To Take If Your Email Account Has Been Hacked
Discovering that your email account has been hacked can be an extremely distressing experience, as it opens the door to serious consequences such as unauthorized access to sensitive information, identity theft, and the potential spread of malware to your device or contacts. When faced with such a situation, your mind may race through various unfortunate possibilities. However, it's essential to remember that there are ways to mitigate risk. It is crucial to respond quickly and decisively to minimize the damage and regain control of your account.
This can include changing your account password immediately, enabling two-factor authentication (2FA) for an extra layer of security, scanning your device for malware, among other things. Below are some common signs of hacking alongside the steps you should take if your account has been hacked. The exact steps of making certain changes in your email account might differ based on the email client you are using, but you should get a general idea of how to proceed.
Common signs your email account has been hacked
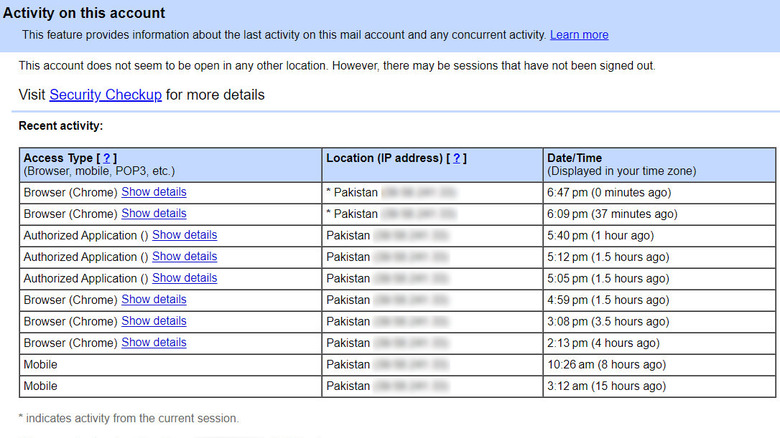
There are several common signs that indicate your email account has been hacked. The first is unusual login activity. If you notice unfamiliar devices or locations accessing your account, it could indicate a problem. Most email providers offer tools to review recent login activity which you can use to monitor your account's security. For instance, here is how you can do it in Gmail:
- Open Gmail and scroll to the bottom of your inbox.
- In the bottom right corner, click on Details. This will open a new window that shows your last account activity. You can see the dates, times, locations, and devices that accessed your Gmail account. You can also see if there are any concurrent sessions or suspicious activities.
Another sign of hacking is unauthorized changes to your account settings. This could include alterations to your password, security questions, or forwarding rules. If you receive notifications about changes you didn't make, it might be a hacker messing around. We also recommend looking at the sent emails from your account, as hackers may use your compromised account to send spam, phishing emails, or malware to your contacts.
In some cases, you may also experience unusual behavior within your account, such as changes to your contacts or inbox organization. You might also notice important emails disappearing from your inbox or trash folder. These changes could be the result of unauthorized access.
Change your password
If you suspect your email account has been hacked, it is best to start with the basics. Start by logging into your email account using a secure device and internet connection. Once logged in, navigate to the account settings or security settings section of your email provider's website. Look for the option to change your password, which is typically labeled as Change Password or Security Settings.
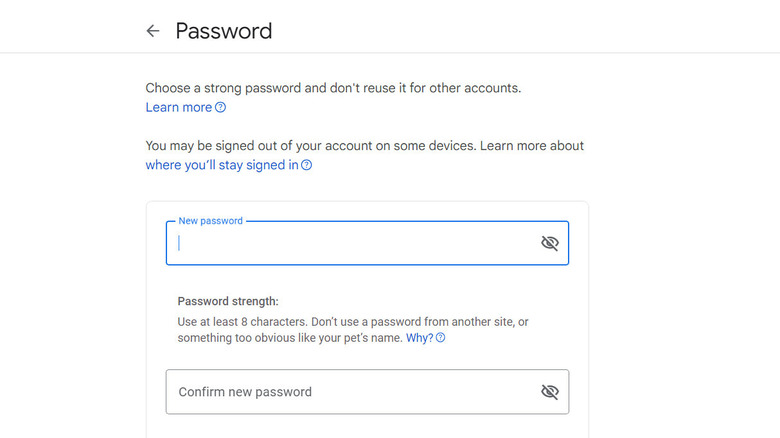
Here is how you can change your Gmail password:
- Sign into your Google account.
- Choose Security from the left pane and head over to the How you sign in to Google section.
- Click Password.
- Log into your Google account again.
- Enter the new password and confirm it.
- Click Change Password.
When choosing a new password, make sure to create a unique one that cannot be guessed easily. It is best to opt for a combination of letters (both uppercase and lowercase), numbers, and special characters. Avoid setting up a short password.
Additionally, consider enabling two-factor authentication (2FA) for an extra layer of security. With 2FA, you'll need to provide a second form of verification, such as a code sent to your phone, in addition to your password when logging into your account. You can find this setting in the Security section of your account. Click 2-step verification and follow the prompts to configure it for your account.
Scan your device for malware
How long has it been since you last scanned your device for malware? If it's been a while or if you can't remember, there is a chance that malware has compromised your device while exposing your sensitive information, including your email credentials. Malware can find its way onto your device through various means, often exploiting vulnerabilities in software, operating systems, or through deceptive tactics.
To check if this is the case, it is essential to scan your device. Start by selecting any one of the reputable antivirus or antimalware programs. There are many options available, both free and paid that can come to the rescue. Once the antivirus or antimalware program is installed and updated, initiate a full system scan to examine all files and programs on your device for any signs of malware infection. Depending on the size of your device's storage and the speed of your computer, the scan may take some time to complete, so be patient.
If any malware is detected during the scan, follow the recommended actions provided by the software to remove or quarantine the malicious files. This can include deleting infected files, isolating them in a secure location, or taking other remedial measures to neutralize the threat. We also recommend taking proactive steps to prevent future infections. Make sure you keep your antivirus/antimalware program up-to-date and avoid downloading programs from unknown sources.
Review the connected apps and accounts
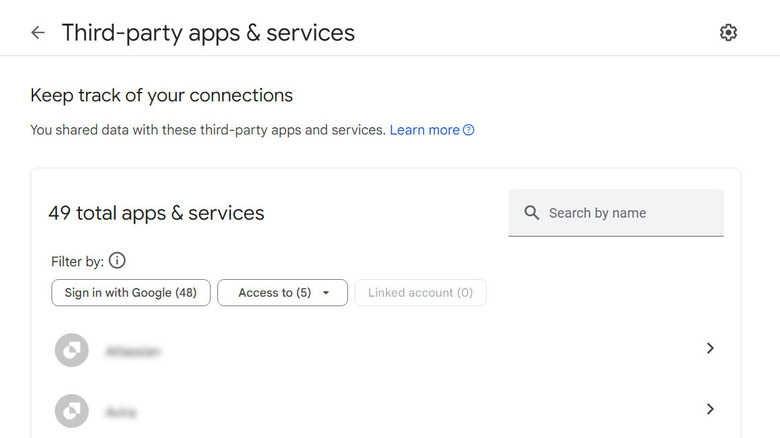
You may have noticed that several apps and services (like email clients, productivity tools, and popular social media platforms) request access to your email account for various purposes. Typically, these include syncing contacts, accessing calendar events, or sending notifications. However, while some apps legitimately require this access to function properly, others may pose security risks or misuse your data.
If your email account has been compromised, consider reviewing connected apps and revoking access to those you no longer trust or need. For this, access the security settings of your email account and navigate to the section for managing connected apps or third-party permissions. Here, you will see a list of all the apps and services that have access to your email account. Take the time to carefully review this list and consider whether each app still requires access or if it's one you no longer use or recognize.
Some email clients (like Gmail) also allow you to view the date and time when the connection was established. If you no longer trust or need an app, click on the Delete all connections with the app option.
In the future, be cautious when granting permissions to new apps and services, and regularly review your connected apps to ensure that only trusted and essential applications have access to your email account.
Let your contacts know about the breach
During the unfortunate events of hacking, you aren't the only one at risk, especially if it is your email address that is hacked. It is not uncommon for hackers to target your contacts as part of their broader malicious efforts.
Once they gain access to your email account, hackers may exploit it to send phishing emails or malware-infected attachments to your contacts. These emails can appear legitimate if they come from your trusted email address, increasing the likelihood that your contacts will interact with them. In case your contacts fall victim to these phishing attempts, hackers can then use their compromised accounts to launch further attacks or gather sensitive information.
Moreover, your contacts may unwittingly become targets of identity theft or financial fraud if they respond to phishing emails or provide sensitive information to hackers posing as you.
To let your contacts know about the breach, you can send an email explaining that you believe your email account may have been compromised or hacked. It is best to encourage them to exercise caution when interacting with any emails or messages they receive from your email account. Advise them to avoid clicking on any suspicious links or downloading attachments from emails that seem out of the ordinary. Alternatively, you can use any one of the secure messaging platforms such as Signal or WhatsApp to notify your contacts about the email breach.
Don't panic
It is completely normal to feel alarmed or anxious upon discovering that your email account has been breached. However, it's essential to remember not to panic as that can cloud your judgment and hinder your ability to take effective action to address the situation.
Firstly, take a deep breath and try to assess the situation objectively. Next, focus on taking immediate steps to secure your email account and prevent further unauthorized access. Apart from the steps we have listed above, you can also consider getting in touch with your email provider's support team or security department to report the breach and seek guidance on the next steps. It is best to provide as much detail as you can about the situation, including any suspicious activity you've observed, such as unauthorized logins or unusual email activity.
They will then advise you on additional security measures to take and may also be able to monitor your account for any further suspicious activity.