MetaPhone Stanford University Crowdsourced Project Shows NSA's Three-Hop Reach
The NSA, through means by which the average citizen cannot tread, has been collecting vast amounts of phone metadata that is intended to help locate and track terrorists and related activity. Though not always keeping up to standard, what the NSA does is not illegal and has been the subject of intense criticism across the globe. In response, Stanford University launched a crowdsourced project to prove the extent of information that can be revealed through the collection of metadata, and using this information has posted a lengthy write up on the three-hops procedure.
MetaPhone is a Stanford Security Lab project, and is dedicated to studying the NSA and its phone records collecting. The idea is that, though being hit with extensive criticism, the National Security Agency has also found its proponents who say that the collection of metadata — which includes things like phone numbers — does not classify as being surveillance, and, in the grand scheme of things, represents very little in terms of privacy violation. In a statement written by Jonathan Mayer and Patrick Mutchler of Stanford University, they and many other computer scientists disagree.
Metadata, says these individuals, is "inherently revealing." To prove this, the MetaPhone project was born, with the goal being to show Congress, the public, and anyone else who pays attention that the phone record collection should not be taking place. The data used in the project is crowdsourced from volunteers who download the MetaPhone app from Google Play, which sends phone logs and social networking information to the project's workers.
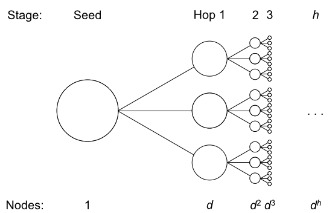
In a write up posted yesterday, the MetaPhone team detailed the NSA's three-hops scheme, which allows the agency to follow one suspicious phone number by up to three hops, which are three degrees of separation from the suspicious number, officially known as a "seed". For each hop, the National Security Agency can nab the full roster of phone records, and the only requirement is that a call was made in the past half decade. Though seemingly simple on the surface, a quick bit of calculations gives one an idea how quickly the NSA can amass phone records.
The idea is that a single seed can lead to three hops, but that each hop can also then lead to its own three hops. As such, a seed that produces three hops then quickly becomes the catalyst by which ever-increasing numbers of hops can take place, and because of the sheer extent of this, one needs to have only made a small number of phone calls. In a testimony reported by the Associated Press back in July, for example, it was demonstrated that if the average number of calls per individual is 40, the NSA's three-hop procedure would allow a single suspicious-individual investigation lead to the collection of over 2 million phone records.
Using the data it collected, the Stanford MetaPhone team set out to test this procedure and see what, exactly, the effects are — essentially, to see how much degree of separation exists between participants, with the expected results being a graph that showed mostly disconnected data points. The opposite turned out to be true, however, and when breaking it all down, the MetaPhone data demonstrated that more than 90-percent of the participants were related in some way in a single graph component. Of that single component, over 10-percent of those who participated were merely two hops separated, and that number grew to more than 65-percent when bumping the hops number up to four or more.
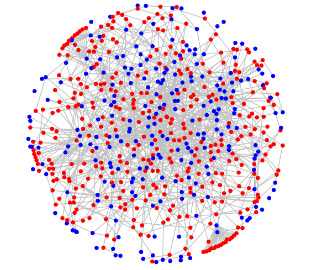
The reason for this is the common linking of individuals through well-known numbers — one example used was T-Mobile's voicemail system through which subscribers end up linked. Outbound Skype calls are also placed through a small roster of numbers, and so any Skype call could also potentially serve as a hop to exponentially high numbers of users. Google authentication calls were another example. To put it simply, said Mayer, "Suppose, for example, that a suspicious number is phoned by a Skype user; a different Skype user has called FedEx; and you have phoned FedEx. You're fair game."
To wrap it all up and put it into perspective, the project's author then pointed to a declassified document that shows an important piece of information related to this: tens of thousands of qualified seed numbers exist.
SOURCE: Web Policy, Stanford and AP
