Gooligan Malware Infects 1m Google Accounts: Here's What To Do
The year is about to end but one of the most potentially harmful Android malware has just started to take flight. If 2015 had its Stagefright exploit, 2016 might be remembered for the Gooligan malware, a portmanteau of "Google" and "hooligan". The malware attacks may have already been in operation since summer and has already installed 30,000 infected apps per day, compromising 13,000 devices daily, and putting more than 1 million Google accounts in danger of being hijacked and their data stolen.
The story of a Gooligan infection starts almost like any other successful malware infection. An unsuspecting user, who should probably know better by now, installs or gets duped into installing a Gooligan-laced app from a third party app store or website. Said app installs a rootkit in an attempt to gain complete access to a device. If successful, the malware proceeds to install more apps from Google Play Store in order to fund its campaign. But more worrying is that Gooligan gives the attacker virtually full access to the user's Google account and all Google services connected to that.
Gooligan is somewhat unique in the way it finances its operations as well as its frightening reach. It isn't just users that the Gooligan malware deceives. Even legit ad servers and systems are similarly conned. Gooligan tries to mimics normal user operations to tap on ads or install sponsored apps in order to receive some cash. It even leaves reviews to make it look more legit (and earn extra too).
That, however, is really only the tip of the iceberg. Once a device has been rooted, Gooligan can gain access to the Google account authentication token associated with the device. That token can then be used to access other Google services, like Docs, Drive, and Gmail, to get to the user's data. This is one case where even two-step authentication can't protect you, as the token system bypasses all that since it makes the user, really the hacker, look like they're already logged in.
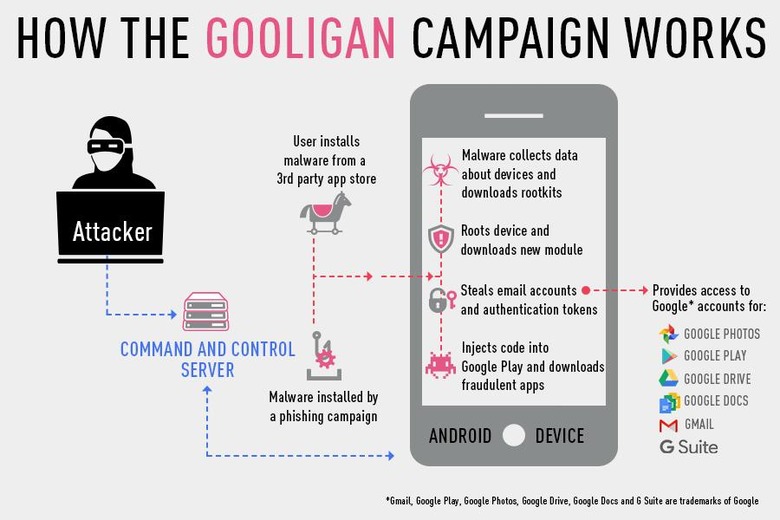
The malware campaign has been discovered and reported by Check Point and has already reached Google's ears. Google director for Android security Adrian Ludwig promised to work with Check Point to plug up this massive hole. So far, however, no formal statement or action has been made. Gooligan can infect any device running Android version 4 to 5, that is, from Jelly Bean to Lollipop, and utilizes rootkits like VROOT and TowelRoot. While these have been mostly addressed in previous security patches, not all of the 74% of devices running these Android versions have received them.
In the meantime, there are a few steps you can take to ensure that your device and Google account remains safe.
• DO NOT install apps from third-party stores (unless you are 200% sure they have their own screening procedure). More importantly, DO NOT just tap on links that claim to download free APKs for apps. And if you notice a suspicious download of an APK, do not install it and delete it immediately.
• Now might be a good time to install some anti-malware app (from Google Play Store, of course).
• Check if you Google account has been compromised. Check Point has provided a handy web page that only asks for your e-mail address to check.
If you are sadly one of the 1 million and still growing compromised users, you have very little recourse:
• "Reformat" (technically, "re-flash") your Android device to its pristine state, either by yourself or through your OEM's certified technicians.
• Change your account password immediately. And while it might not help in this particular case, now might be a good time to enable two-factor authentication as well.
Check Point has provided a rather long list of fake apps infected by Gooligan. These are mostly apps that have been downloaded from other sources, but do check if you have them installed as well.
• Perfect Cleaner
• Demo
• WiFi Enhancer
• Snake
• gla.pev.zvh
• Html5 Games
• Demm
• memory booster
• แข่งรถสุดโหด
• StopWatch
• Clear
• ballSmove_004
• Flashlight Free
• memory booste
• Touch Beauty
• Demoad
• Small Blue Point
• Battery Monitor
• 清理大师
• UC Mini
• Shadow Crush
• Sex Photo
• 小白点
• tub.ajy.ics
• Hip Good
• Memory Booster
• phone booster
• SettingService
• Wifi Master
• Fruit Slots
• System Booster
• Dircet Browser
• FUNNY DROPS
• Puzzle Bubble-Pet Paradise
• GPS
• Light Browser
• Clean Master
• YouTube Downloader
• KXService
• Best Wallpapers
• Smart Touch
• Light Advanced
• SmartFolder
• youtubeplayer
• Beautiful Alarm
• PronClub
• Detecting instrument
• Calculator
• GPS Speed
• Fast Cleaner
• Blue Point
• CakeSweety
• Pedometer
• Compass Lite
• Fingerprint unlock
• PornClub
• com.browser.provider
• Assistive Touch
• Sex Cademy
• OneKeyLock
• Wifi Speed Pro
• Minibooster
• com.so.itouch
• com.fabullacop.loudcallernameringtone
• Kiss Browser
• Weather
• Chrono Marker
• Slots Mania
• Multifunction Flashlight
• So Hot
• HotH5Games
• Swamm Browser
• Billiards
• TcashDemo
• Sexy hot wallpaper
• Wifi Accelerate
• Simple Calculator
• Daily Racing
• Talking Tom 3
• com.example.ddeo
• Test
• Hot Photo
• QPlay
• Virtual
• Music Cloud
SOURCE: Check Point
