Dell BIOSConnect vulnerability threatens millions of PCs
Dell is one of the world's biggest PC vendors and its laptops number in the millions. That means that there are also millions of potential victims ripe for the picking should hackers get hold of a security exploit that affects almost all of them. That opportunity might have finally come up when Dell's own software in charge of keeping users safe the moment a computer boots is itself compromised, opening the door for hackers to get in without being detected.
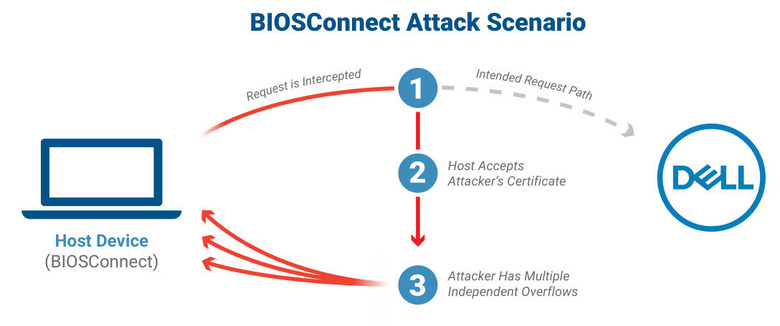
At the heart of this latest vulnerability report is Dell's BIOSConnect, a part of its SupportAssist software that's pre-installed on almost all Dell computers running Windows. BIOSConnect itself has only one task and that's to provide remote firmware updates and OS recovery functionality. Given how computers startup at the BIOS level, getting control of this stage of the bootup process means getting control of the entire system in the long run.
That's exactly the case that Bleeping Computer is reporting, where a hacker can intercept BIOSConnect's communication and trigger overflow exploits. This can happen when users try to use remote OS recovery or when trying to update the Dell computer's firmware. A compromised BIOS or UEFI firmware could then masquerade as legit software to Dell's and Windows' security systems.
Security researchers from Eclypsium who reported the vulnerabilities recommend that Dell users avoid using BIOSConnect entirely. There are multiple ways to update the computer's BIOS or UEFI firmware and the utility only offers conveniences that may not be worth the security risk. Dell is issuing BIOS/UEFI updates on its website for affected models.
Bleeping Computer notes that this isn't the first time a part of Dell's SupportAssist is revealed to have some critical security flaw. Dell's pre-installed software has been reported to have one vulnerability or another but such a situation is sadly common among many OEM's utilities, even those designed to protect users.
