Cloak & Dagger Exploits Android Accessibility, Overlay Features
The phrase "cloak and dagger" is often used to refer to acts of subterfuge and espionage, almost always naughty things. That term is indeed apt for this latest set of exploits on Android that use those tactics to ensnare unwitting users. A set of vulnerabilities rather than a single one, these exploits abuse otherwise useful, even critical, features of the Android platform to do their nefarious deeds, successfully hiding themselves even from more vigilant users.
The good news: Google is already aware of the situation. The bad news: aside from a few vulnerabilities that have already been plugged up, there's little that Google can do without actually making Android itself harder to use. That's because these exploits use features inherent in Android's accessibility system as well as its overlays architecture to trick users into enabling features or even typing in confidential information.
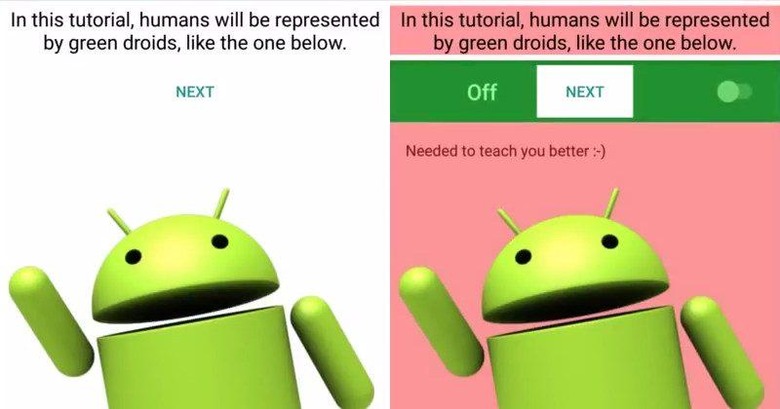
In addition to its already open nature, the Android platform offers additional hooks that can be used for certain cases. Accessibility functions, for example, are necessary to allow the device to be used by those with physical handicaps. Overlays, on the other hand, have been a rather controversial feature that allowed interactive elements to be placed on top of other parts of the screen, like the sometimes notorious chat heads.
The cloak and dagger set of vulnerabilities target these two features in particular in order to gain access to user's sensitive data. An app from an unverified source, for example, can use an overlay attack to fool the user into enabling accessibility access for a hidden malicious app. Once acquired, the app can use those accessibility features to log keystrokes, stealt two-factor authentication, and more.
It is rather unfortunate that Google can't easily resolve the matter without breaking essential parts of the Android platform. Now that the word is out, however, Google might be forced to try and find a better compromise. Until then, prevention is going to be better than cure. Make sure that installing APKs from unverified sources is disabled by default and only enable it for packages you completely trust and then disable it afterwards.
SOURCE: Georgia Tech