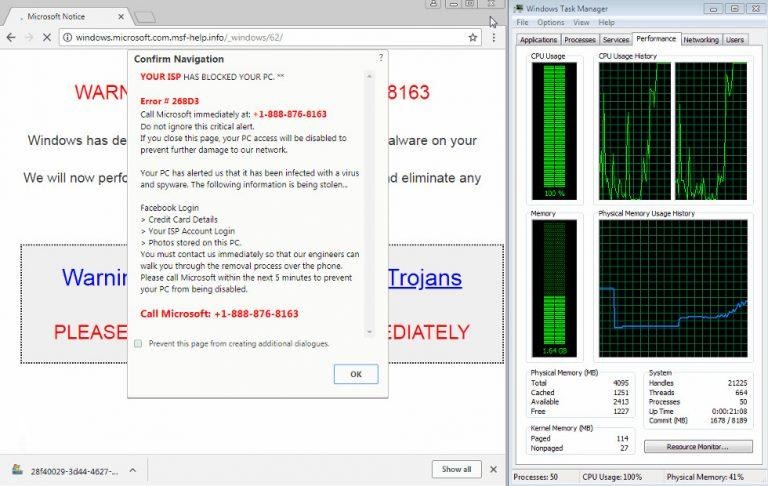
Chrome browser locker scams users into calling number
Browser users are often the easiest kind of users to trick. Many of them are not as tech savvy and are often careless in the links they click. As browser makers like Google and Mozilla step up their efforts to fight off phishing, scams, and malware, so do scammers level up in their creativity and cunning. One new technique that is gaining popularity is actually almost too simple and unsophisticated. But that simplicity is also the key to its success in tricking users to call a "toll-free" phone number by simply locking up or freezing their web browser.
When confronted with a warning about how their security has been compromised, less informed users are likely to take the scam bait. Throw in a barrage of popups or an unresponsive web browser, and you're guaranteed to have a new victim. The latter is what some scammers are now doing to con users and, ironically, they're simply using what web browsers have available already.
They aren't exactly injecting malicious code into browsers or computers. Instead, they're simply abusing API, i.e. programming functions, provided by browsers, in this case, Google Chrome. In this particular instance, the process that locks up a browser is almost genius in its simplicity. It takes advantage of such an API and starts thousands of downloads in rapid succession, causing Chrome to become unresponsive in just a matter of seconds.
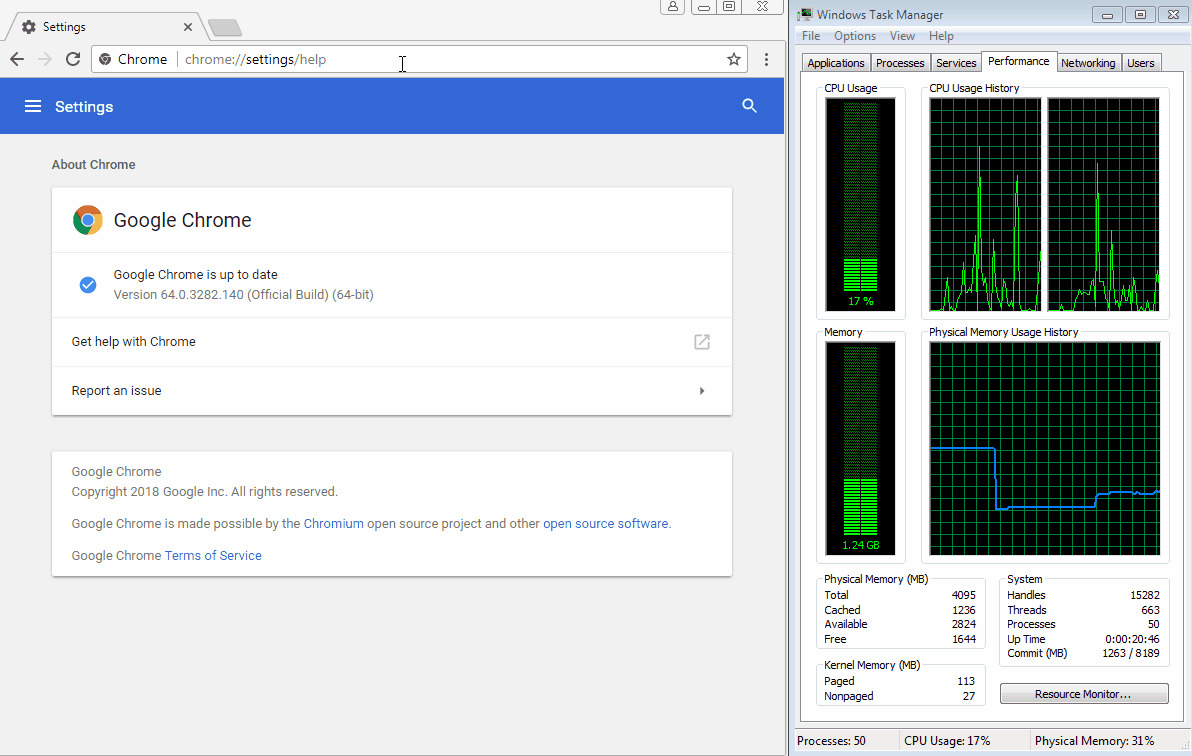
Other than burning up CPU cycles, the attack is almost harmless. More powerful computers will be able to handle the load long enough for users to stop it. More knowledgeable users can kill the Chrome browser via the Windows Task Manager. Majority of users, however, might panic, and that's more than enough for them to call the number on the fake warning popped up by the malicious website.
Like any other security vulnerability, it's a game of cat and mouse. Google patches one API and scammers look for a new API to abuse. This particular flaw seems to only affect Google Chrome on Windows, but scammers can load different pages for different browsers, abusing vulnerabilities specific to those browsers as well.
SOURCE: Malwarebytes