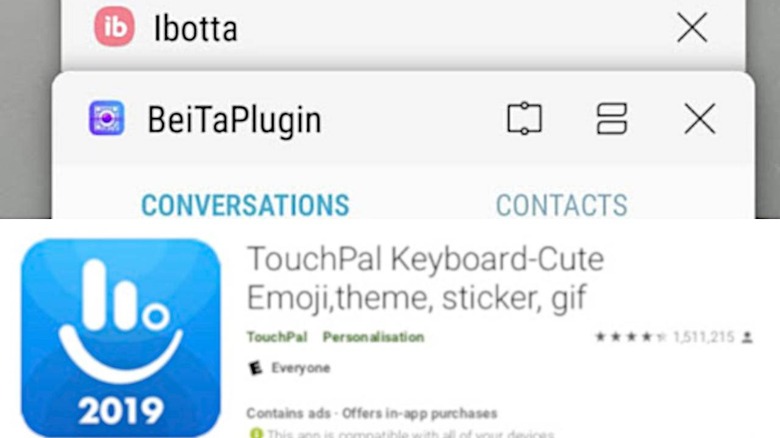
BeiTaAd adware discovered in 238 Google Play Store apps
It's probably nothing new by now whenever news about this or that malware getting into Google Play Store's automated "bouncer" but few have probably achieved the same mass reach as this one. Called BeiTaAd or BeitaPlugin, the particular strain of adware will perhaps go down in history for having taking great pains to hide its nature from security measures and being found in 238 unique apps. It is, perhaps, no coincidence that those apps were all made by the same Chinese company as well.
Admittedly, not all of that 238 apps are what you'd normally call "apps". A large majority of those "infected" by BeitaPlugin were add-ons to the TouchPal keyboard developed by Shanghai-based CooTek. And, yes, all those 238 apps and the BeitaPlugin itself, according to Lookout Security, were developed by CooTek as well.
BeiTaAd may not be as destructive as some malware but it is just as harmful. The ads that it serves appear not only when you're using the apps that ship with the plugin but even on lock screens and phone calls, places where Google would explicitly prohibit displaying ads (unless it's a lock screen or phone app). The ads disrupt the user experience and take up resources that could be used for other, more important processes.
Even more worrying, however, is how the great lengths its developer, presumably CooTek, goes through to hide its existence from Google and other security apps. It utilizes methods such as encrypting the plugin and renaming it to some seemingly harmless file type, like an image. And it wasn't just a one time thing. The plugin seems to be actively developed and modified to escape detection..
The plugin has reportedly been removed from affected apps but not before those have had around 400 million downloads in total. Google definitely needs to step up its game in the fight against malware, especially when developers do everything technically possible to get away with anything.