Kemoge adware infects Android phones by rooting them
Adware, or malicious programs designed to serve ads and gain user information, aren't exactly new, especially on Android. Most are a nuisance at best, but some do make a lot of damage. Security firm FireEye has stumbled on yet another one of the latter class. Dubbed Kemoge, from the command and control or CnC server that it communicates with, this particular malware has one rather frightening ability beyond incessantly flooding you with ads. It can actually root vulnerable devices, which practically gives hackers a direct open door into the device.
Like any other adware, the process starts innocently enough, depending on what you define by innocent. Kemoge-infected apps can masquerade themselves as popular apps and then get uploading into third party app stores as well as ads that can install apps on smartphones. In other words, sources that do not take advantage of the security protection and app scanning that Google provides. That said, there is at least one instance where such an infected app actually made it to Google Play Store, but with less dire effects.
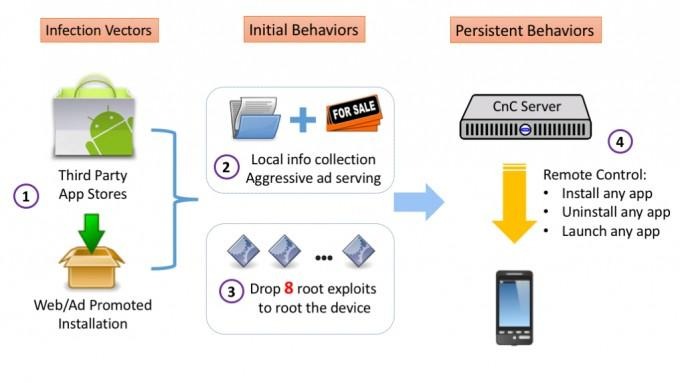
And like any other adware, Kemoge aggressively serves you ads, which pops up in random instances and places, even when you're just in your home screen. What makes this adware slightly different is that in addition to that, it also tries to root the infected devices using known security exploits. For the uninitiated, rooting is the process of gaining superuser privileges (or "root" in UNIX/Linux parlance), pretty much like jailbreaking on iOS. And like jailbreaking, gaining root happens through security exploits. Now, there are more documented and safer ways to gain root, but there are also more perverse exploits that get admin privileges without the user knowing it.
Once a device is rooted, it is pretty much fair game to any hacker using Kemoge. In addition to communicating with a remote server to deliver the user's information, Kemoge can also be used to install apps without user consent or even knowledge. It can actually even uninstall apps with the same freedom, and it is usually programmed to uninstall anti-virus apps to avoid detection and removal.
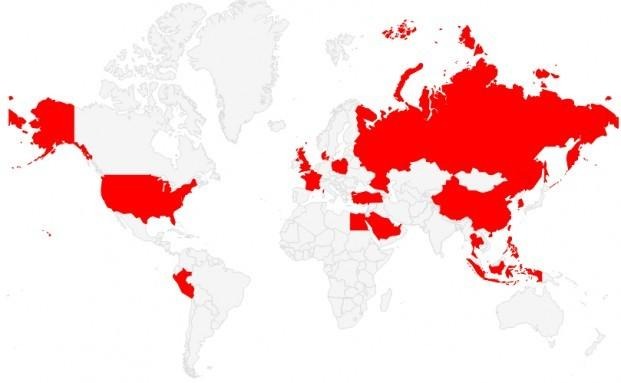
FireEye says that the infection coverage of Kemoge actually spans a good number of countries across the whole world. It has also traced part of the malware's origins to China. At the moment, the blog doesn't offer any method to remove the malware, perhaps except for wiping the infected device clean. It does advise users not to install apps from third party sites, especially shady ones, and to keep their devices up to date to close those known root exploits.
SOURCE: FIreEye
