XcodeGhost malware gets past Apple App Store scrutiny [UPDATE]
Apple's stringent and sometimes even heavy handed review rules for iOS apps have both been hailed and criticized alike, but its core benefit remains the same, very few malicious apps gets past quality control. However, it's not infallible, as five past iOS malware can attest to. Now a sixth joins that list, but with more far-reaching consequences. Dozens, if not hundreds, of App Store apps, specifically in China, might be infected by the XcodeGhost malware, and this time, the apps are otherwise legitimate ones and their developers unwitting accomplices. All thanks to an unofficial Xcode installer going around the Internet.
Xcode is Apple's official software development tool, whether for OS X or iOS apps. The problem with Xcode, at least for Chinese app developers, is that its 3 GB installer downloads too slowly. They therefore resort to unofficial mirrors of the installer floating around a Baidu-run cloud hosting service. Little do they know that this particular installer has been modified to contaminate otherwise legitimate and clean iOS apps with malware without the developers' knowledge. Worse, apps infected with XcodeGhost manage to bypass the usual strict review process, allowing apps to go public on the App Store containing the malware.
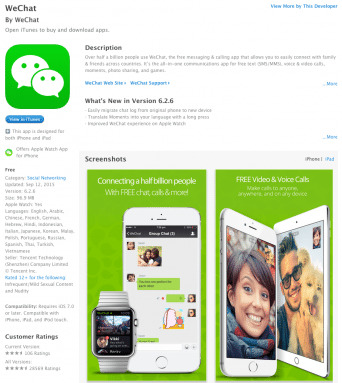
At first it seemed that XcodeGhost was relatively harmless. It did harvest some device information, like the current time, the infected app's name, and the device UUID, and sent those to remote server. Further analysis revealed, however, that XcodeGhost could actually do more than that, like display a fake prompt to get users to enter their credentials, or even read from the clipboard in case the user copies and pastes his or her password. Examples of apps that have used the tainted Xcode installer include popular ones like Tencent's WeChat and NetEase Cloud Music App, just to name among the few dozens that have so far been identified. The number potentially reaches 344 apps, according to Chinese security firm Qihoo360.
XcodeGhost's damage, however, has more far-reaching consequences beyond this single instance. Since enterprise iOS apps are distributed without App Store reviews, tainted apps can be more easily spread to employees' iPhones. But more than that, developers might not even need to download the infected Xcode installer to become unwilling malware carriers. XcodeGhost actually exploits a specific Xcode behavior that scans certain system directories for files to be included in building an app. This means that OS X malware, which is more easily installed an iOS one, can potentially compromise even a legit Xcode installation.
Apple has already pulled out the infected apps from the Chinese App Store but the situation might have already opened a can of worms. Developers, of course, should only use tools downloaded from legitimate sources, but Apple might also have to patch Xcode itself to plug up this hole. And considering how much it's targeting the Chinese market, it perhaps should provide faster means to download Xcode so that developers won't have to search elsewhere.
UPDATE: WeChat reached out to SlashGear to reassure its customers that the latest versions of the messaging apps, specifically version 2.6.6 and higher, are unaffected by this issue. Only version 2.6.5 is tainted by XcodeGhost so users are advised to immediately update their WeChat apps. WeChat also claims that so far no data theft or leak has been observed related to this malware.
SOURCE: Palo Alto Networks
VIA: Reuters