SMB v1 vulnerability won't be fixed, here's how to disable it
Most of the time, when software vendors receive a report of a vulnerability, especially a serious one, they usually move swiftly in order to plug up the hole. There are times, however, when a vendor might decide that the cost of patching up the vulnerability and distributing that fix is far more trouble than it's worth. That seems to be the line of thinking Microsoft has adopted regarding a 20-year old SMB bug that affects every Windows machine dating back to 2000, leaving it up users to protect themselves.
To be clear, it is only the first and oldest version of SMB, a.k.a. SMBv1 that's affected. SMB stands for Server Message Block and is a technology used to share files over a network, usually between Windows computers. At this year's DEF CON Hacker Conference, RiskSense security researchers introduced a vulnerability they nicknamed "SMBloris" that could could take down a Windows machine with a simple Denial of Service or DoS attack.
Such attacks have become a staple in news, even mainstream ones but it is actually a more modern variant of it that is more popular, the Distributed Denial of Service or DDoS attack. A DoS attack works by sending massive amounts of service requests more than a server can handle, causing it to crash. Such attacks usually involve using multiple computers from different locations to send the requests, hence being distributed. SMBlori, however, is so old that it actually needs only a single, low-power computer, like a Raspberry Pi, to initiate a DoS attack.
That's partly why Microsoft has downplayed the severity of vulnerability. Which is a bit ironic because the researchers proved how a simple single-board computer can take down a powerful server. But there's one other reason why Microsoft doesn't want to even lift a finger: it's too easy to turn it off.
While SMB is still in use today, SMBv1 is so old that Microsoft simply recommends turning it off if you don't use it anyway. And since it won't be releasing a patch to fix SMBv1, you might as well do it. Here's how.
1. Open up Control Panel (from the Start Menu or by searching)
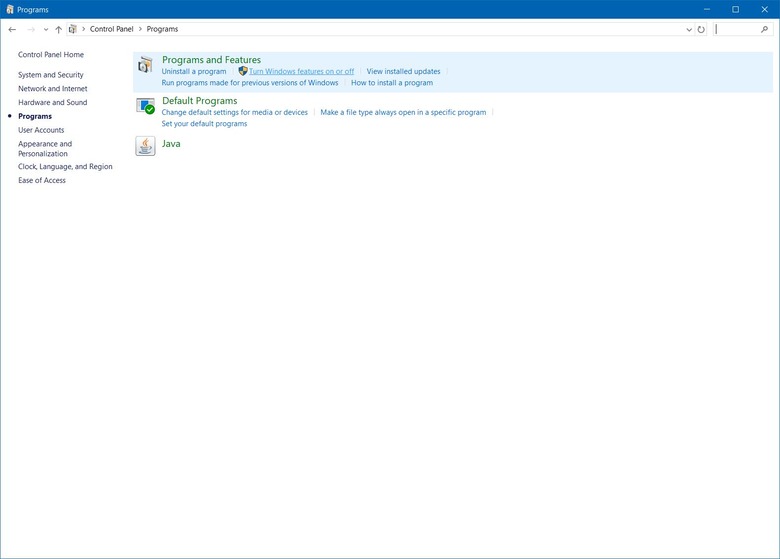
2. Go to the Programs group
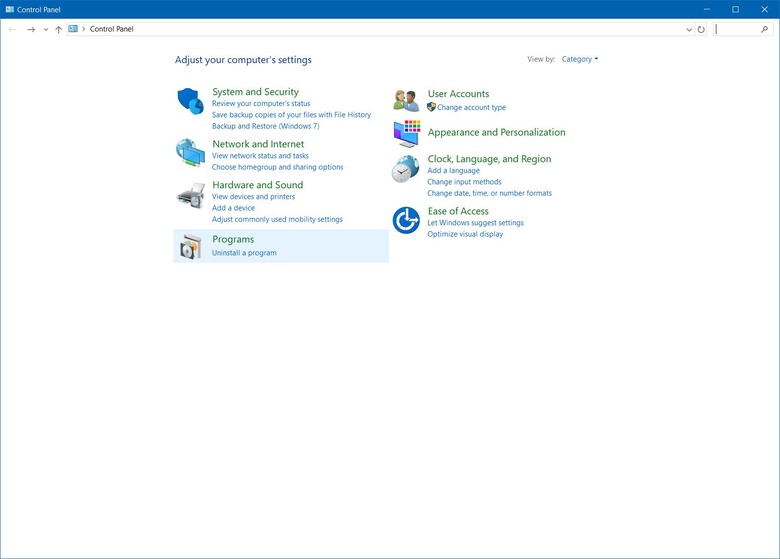
3. Select Turn Windows features on or off under Programs and Features.
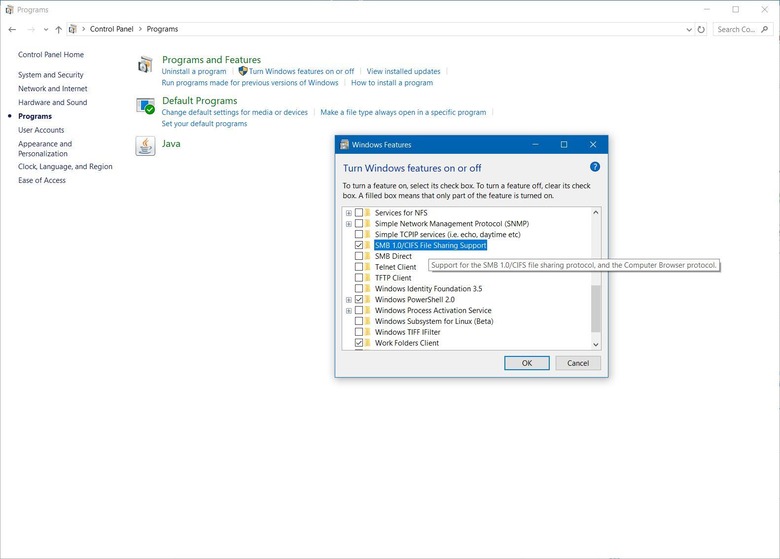
4. Look for SMB 1/CIFS File Sharing Support and uncheck it
5. Reboot
While it is indeed that easy to disable the ancient feature, it's only easy if you know about it in the first place or why you should disable it. It is indeed better if Microsoft fire off an update that does that for users, with their permission, but it seems that it has already decided to let users sweat over it themselves.
VIA: Security Affairs