Originator of web's Password Rules admits he was wrong
A complicated, mixed up password is not any more secure than a password that's all lower-cased letters. The reason the internet told us (and continues to tell us) to make a password with numbers and capital and lower-cased characters and punctuation in it is a paper called "Digital Identity Guidelines." This nightmare of a paper was published at the National Institute of Standards and Technology (NIST), and the rules therein were based on pre-digital age security nonsense.
Bill Burr's Misconceptions
The writer of that paper was a man named Bill Burr, (no relation to the comedian), a former manager at NIST. This document somehow made internet passwords – and thereby most computer-based passwords – the needlessly complicated monsters they are today. The rules in question can be found in the NIST document "Digital Identity Guidelines". This is an official government document from the U.S. Department of Commerce.
This document goes through a bunch of ways in which passwords should be chosen – there's a whole bunch of other neat stuff in there about security, too. Back in 2003 in this since-updated document, Burr recommended using complicated passwords with a mix of capital letters, lower-cased letters, non-alphabetic symbols, and numbers. He suggested then that using these characters would make passwords more difficult for malicious agents to guess.
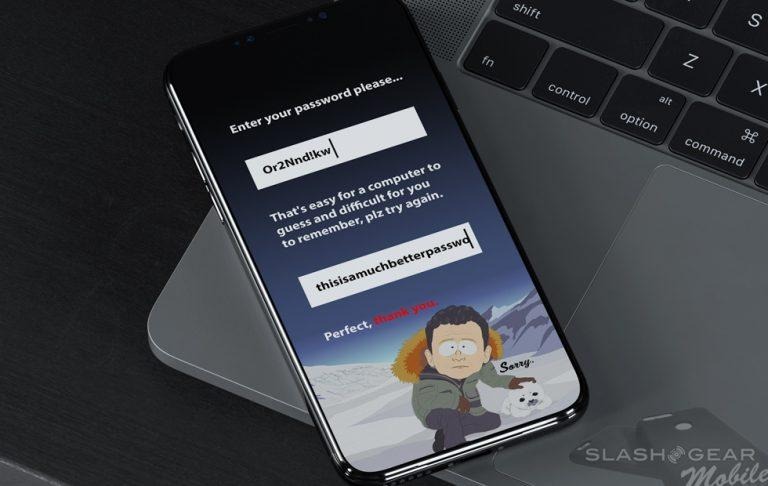
Here in 2017, one of modern hacker's most basic tools – a bruteforce attack – can guess a short password in very little time, regardless of the odd mix of characters it uses. Instead of picking a short password that's difficult to remember, making a long password is best. This is especially true if the password is something unique that only one person would think to type. Human words with letters that make a sentence, for example.A password such as "thisroomsmellsliketerriblefarts" is better than one like "W9ob!R55". Special characters, capitalization, and a mix of letters and numbers do NOT make a password more difficult for a computer to guess, they only make a password harder for humans to remember.
Burr Apologizes
"Much of what I did I now regret," said Burr in an interview with the WSJ this week. "In the end, it was probably too complicated for a lot of folks to understand very well, and the truth is, it was barking up the wrong tree."
In this interview Burr suggested that his research for this document came mostly from a white paper published in the 1980s. Well before we needed passwords for access to our email, online bank accounts, social networks, and smartphones.
Burr's contributions to the document also suggested changing one's password from time to time. But changing one character in a short, complicated password does not a more secure password make. It is only the length of the password that matters. The longer the password, the longer it takes for a machine to suss it out.
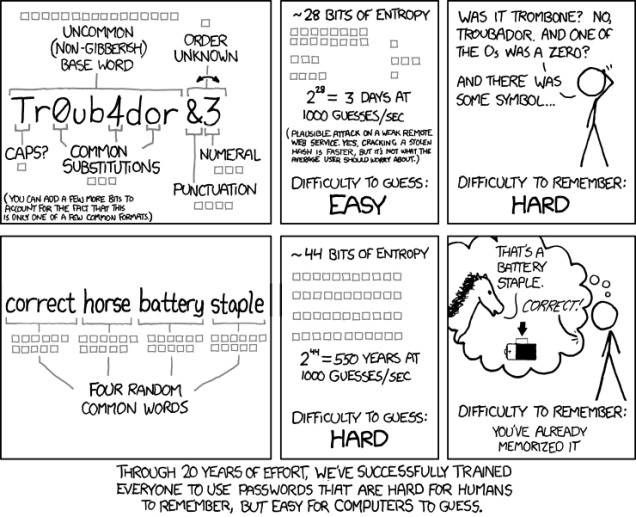
As is generally the case when it comes to explaining tech and science-related things in a simple manner, XKCD did it years ago. Check the password-infused comic above. This comic comes from XKCD and was published under a Creative Commons 2.5 license.
The New Style - multiple checks
*In August of 2017, these security guidelines have been updated. Included in the document is a much more modern look at how computer access security works in 2017. The document mentions legacy requirements and how the world has changed (since 2003).
"Access authorization to computers and data has traditionally been based on identities authenticated through user selected passwords," said the document. "More recently, cryptographic mechanisms and biometric techniques have been used in physical and logical security applications, replacing or supplementing the traditional identity credentials."
Also in the document is a link to FIPS: Personal Identity Verification (PIV) of Federal Employees and Contractors. This paper is another official US government document, this time part of Federal Information Processing Standards (FIPS). There it is shown (at the time this article was first published) how federal security standards rely on three factors of authentication.
The three main categories of Multifactor Authentication (MFA):• Something you are (example: Fingerprint)• Something you know (example: PIN code)• Something you have (example: Security Card)
While lengthier passwords are best for the average citizen, the federal government recommends multiple forms of authentication for access to any important information both on and off the Internet. Also of note here – these documents are always subject to updates and improvements. As the initial document said at its latest update, "Updates to authentication and assertion requirements to reflect advances in both security technology and threats."
Nutshelled
The guy who's responsibility it is that we're using insanely complicated passwords has recanted. He basically said he was sorry for wasting our precious time for the past 14 years. Mixing letters, numbers, and odd characters do not make passwords more secure, and the most secure password (when using one-factor authentication) is a password that's long.
And after all that, if you use the password "passwordpasswordpassword", may whatever god you believe in have mercy on your soul.