Nitro hack steals R&D and defense secrets
Hackers used email scams distributing a notorious malware tool to steal research & development secrets from chemical manufacturers, defense companies and other targets in a huge industrial espionage attack dubbed Nitro, it has been revealed. Poison Ivy, a Windows-based trojan which allows covert remote access to infected PCs, was distributed among firms between April and September this year, according to a new paper [pdf link] from security firm Symantec, with 29 chemical sector companies and a further 19 – primarily in defense – in other sectors targeted.
Although a full list of the originally targeted companies has not been revealed – though it is believed to be more than the 48 impacted – the victims include Fortune 100 firms working on chemical research, those involved in the development and production of materials used in military vehicles, and manufacturing infrastructure specialists. In short, it seems the hackers were looking for a shortcut into the latest tiers of chemical compound development.
"This attack campaign focused on the chemical sector with the goal of obtaining sensitive documents such as proprietary designs, formulas, and manufacturing processes" Symantec
Staff at the companies were targeted with emails suggesting they needed to update Flash, their anti-virus software or other services; in fact, they were loading Poison Ivy onto their computers. The malware quietly opens a network port and waits for contact from a command server which, in this case, Symantec says was located in the US but run by a Chinese hacker.
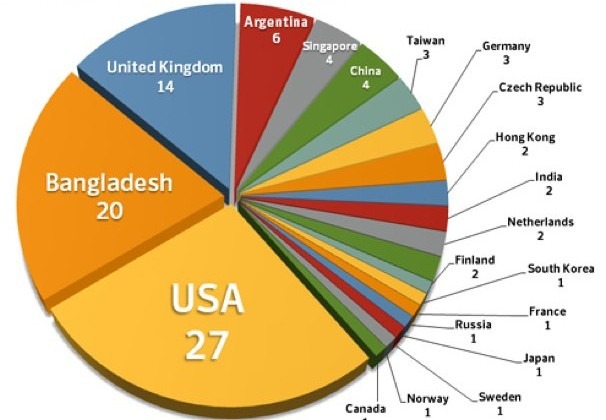
It's possible, the security firm suggests, that the hacker is in fact working with a group or is a decoy to mask the real identity of those behind the attack. Infected companies are spread across the globe, with the majority in the US, Bangladesh and the UK.
[via Computerworld]