Digital camera ransomware shows another way hackers could ruin your day
Your digital camera may not steal souls every time you take someone's photos, but it may present an unexpected opportunity for hackers to load ransomware. New research suggests that increasingly consumer-friendly features like wireless connectivity are opening up DSLRs to potential hacks, that could leave your photos locked behind a ransom paywall or worse.
Indeed, it needn't only be wireless. USB attacks are another potential point of entry, as owners plug their digital cameras into a PC in order to retrieve images saved on it, or to install new firmware.
Security firm Check Point Research decided to explore how straightforward it might be for someone with nefarious intent to compromise a camera, and discovered that it wasn't as difficult as you might hope. Increasingly complex camera technology, but a blindspot by users – and manufacturers – that modern DSLRs could be susceptible to attacks leave owners potentially vulnerable.
Part of the problem is that the security mindset hasn't necessarily kept up with the development of new convenience features for cameras. WiFi being added to wirelessly share images with a phone or computer, for example, has opened up PTP (Picture Transfer Protocol) to potential wireless hacks, too. PTP was initially designed to make image transfers over a USB cable more straightforward.
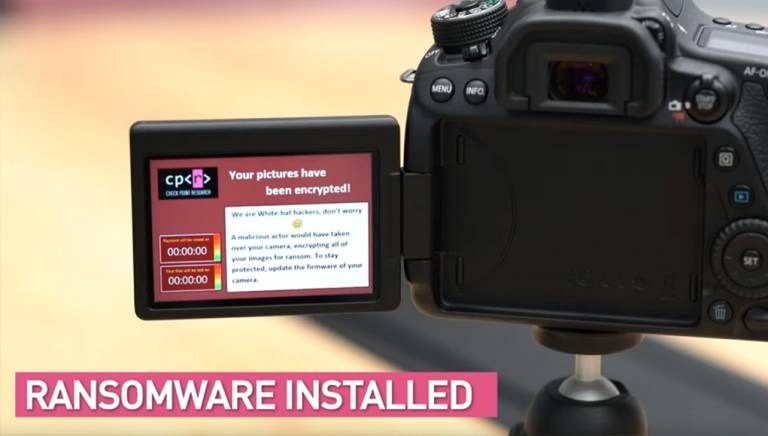
Check Point Research decided to focus on PTP's potential for nefarious use, and targeted a Canon EOS 80D DSLR as the victim. It wasn't a casual choice, either. Canon has more than 50-percent of the DSLR market, for instance, the EOS 80D has WiFi support along with USB, and the Magic Lantern aftermarket modding community has deeply explored its firmware. That makes it both a well-documented and broadly-deployed potential target.
Actually coming up with a hack wasn't exactly straightforward, even so, but in the end the team of researchers had a system which could mimic the firmware update process for the EOS 80D but instead encrypt all the files saved on its memory card. A ransom message could then be shown on the display, demanding payment in return for unlocking the images again.
Canon was notified of the potential exploit before it was publicly disclosed, and released patches for its cameras earlier in August. The advice is that it's best to install this new firmware to avoid possible ransomware.
All the same, this isn't just about one type of camera from one company. "Our research shows that any "smart" device, in our case a DSLR camera, is susceptible to attacks," Check Point Research's Eyal Itkin writes. "The combination of price, sensitive contents, and wide-spread consumer audience makes cameras a lucrative target for attackers."