DARPA's "Dark Web" revealing Memex tool is also pretty scary
In the realm of cybersecurity, balancing national security and personal privacy is undoubtedly a tough act to pull off. The Internet has long been held as the bastion of free speech, but it has also become a breeding ground and hiding place for miscreants. So it isn't surprising that law enforcers would want to penetrate all corners of the Web in order to catch the bad guys. That is exactly what DARPA's new search engine called Memex is trying to do, by diving even into the depths of the "Dark Web".
DARPA or Defense Advanced Research Projects Agency, is the Department of Defense's research arm and considered to be the root of the Internet. It is almost fitting that such a tool that crawls through the entire Internet would come from it. DARPA has been at the forefront of developing software that, at least in purpose, would help the government find and take down criminals that try to hide behind the Web.
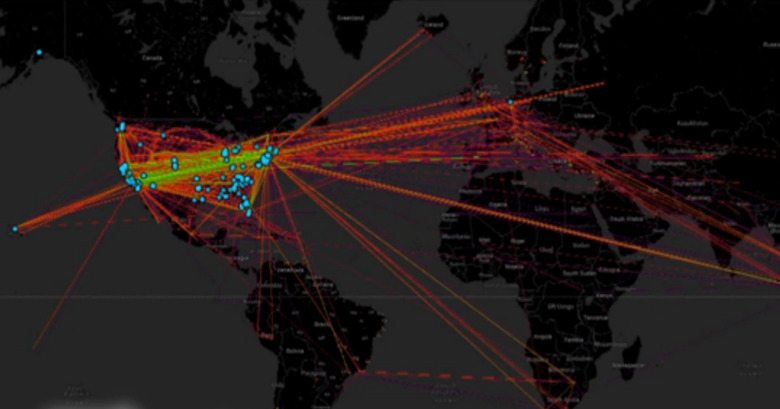
According to Memex creator Chris White, what we regular users see through search engines is just 5 percent of what the Web really contains. A lot of shadowy corners and invisible places, ominously called the "Dark Web", has become home to illegal activities. The goal of the Memex search engine then is to be come a super search engine that can actually trace deeper than most search engines can. Click on just 5 links and it will yield 50 more related links. It can be used to create a visual representation of links across the country and even across the world, showing the relationships and even movement of certain websites.
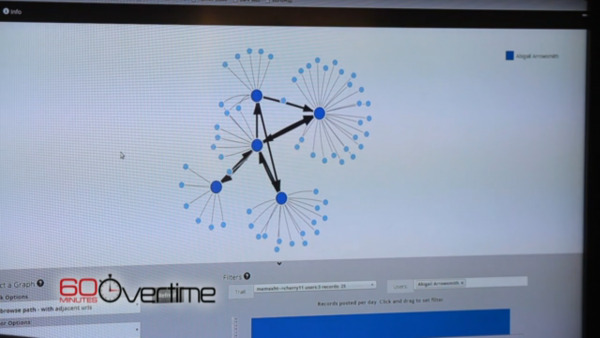
Memex is designed, at least initially, to help fight sex trafficking. It can try to follow, say, a photo of young woman as it travels through the Internet and even physically through the country. It might be a strange project for the DoD, but the line of reasoning is that the people involved in sex trafficking are also likely to be involved in arms smuggling and other threats against national security.
Memex might be a fascinating and powerful tool, but, like any other tool, it can be used for good or for ill. That same technology can very well be put to use to invade privacy and trace the flow of legitimate and private data. In the right hands, it can be a weapon to combat crime. But sometimes even governments aren't the right hands.
SOURCE: CBS News