Apple denies opening NSA backdoor to iPhone
Apple has denied collaborating with the NSA to add a snooping backdoor to the iPhone, insisting that despite allegations that the DROPOUTJEEP program could access large swathes of iPhone content without the user realizing, it is unaware of any such exploit. New leaks from NSA documents acquired by whistleblower Edward Snowden led to claims earlier this week that the NSA had a tool that could access data like text messages, location, and more with "100-percent success," something Apple strongly denies either facilitating or, indeed, knowing was in operation.
In fact, in a statement given to TechCrunch and AllThingsD, Apple effectively describes the NSA as "malicious hackers" and says it will work to "defend" users from any attempts to insidiously access iOS content. The Cupertino company is investigating the allegations, it says.
"Apple has never worked with the NSA to create a backdoor in any of our products, including iPhone. Additionally, we have been unaware of this alleged NSA program targeting our products. We care deeply about our customers' privacy and security. Our team is continuously working to make our products even more secure, and we make it easy for customers to keep their software up to date with the latest advancements. Whenever we hear about attempts to undermine Apple's industry-leading security, we thoroughly investigate and take appropriate steps to protect our customers. We will continue to use our resources to stay ahead of malicious hackers and defend our customers from security attacks, regardless of who's behind them" Apple
The original documents did not confirm Apple collaboration, but the suggestion of consistent access was seen by some as indicating some degree of assistance in the underlying architecture of iOS.
Meanwhile there are also lingering questions as to just how recently the NSA supposedly had iPhone access. The leaked paperwork is dated 2008, and there's obviously no mention of any iOS version beyond 5; the NSA's DROPOUTJEEP system also apparently required physical access to the iPhone itself for installation.
A remote-installation system was a work-in-progress, according to the leak, but was not functional as of 2008.
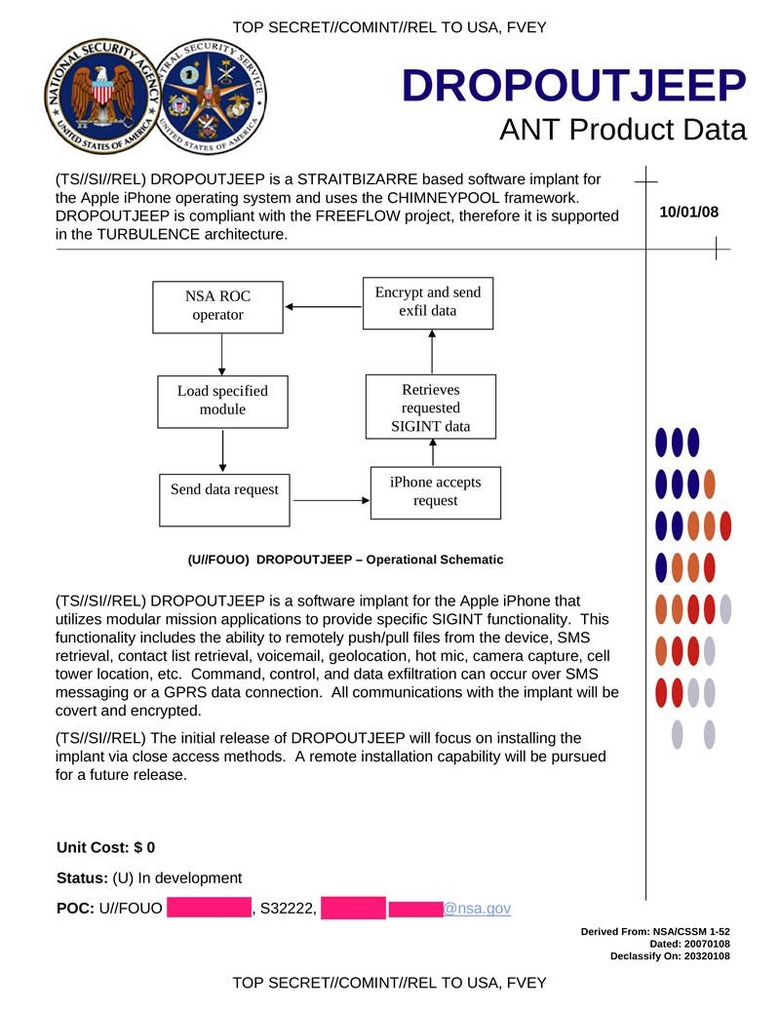
Nonetheless, the extent to which the NSA could compromise "infected" iPhones was surprising. As well as accessing text messages, contacts lists, and GPS/cell-tower location, the DROPOUTJEEP tool could access voicemails, turn on the microphone to monitor audio in the surrounding area, and take photos using the smartphone's camera.
It's not the first time Apple has reacted to compromised iPhone claims. Earlier this year, the company strongly denied any PRISM backdoor or iMessage monitoring, pointing out that its IM service was end-to-end encrypted. Security researchers highlighted the potential for cracking that encryption later in the year, but Apple said it had not created the tool to do such tracking.
