Advertising scripts using data from browser password managers to track users
It's well-known that tools like password managers can help users improve their online security — by creating unique passwords for each website. However, researchers have found that advertising trackers are able to exploit data from the simplified password managers built into browsers like Chrome and Firefox (rather than standalone services like 1Password and LastPass) to continue tracking users browsing habits across the internet.
Browser-based password managers are designed to automatically detect a website's username and password fields, and then fill in the stored information. Computer scientists from Princeton's Center for Information Technology Policy write that they've found ad tracking scripts that manage to hide invisible login forms on a webpage, and then record the record the data autofilled by the browser.
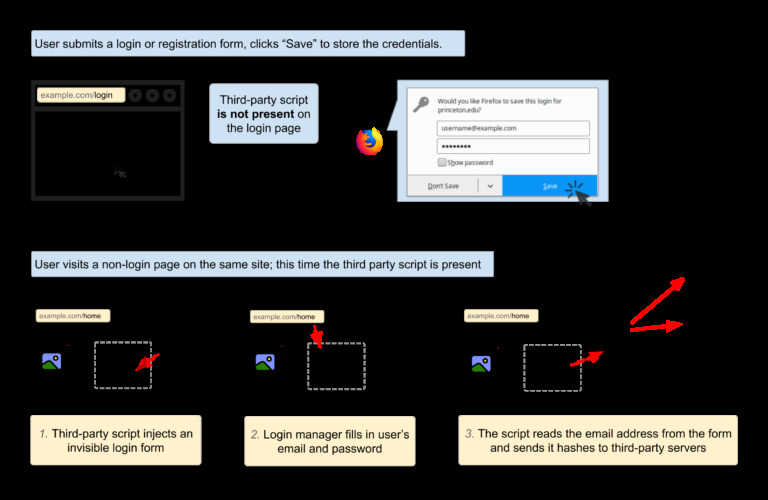
The researchers identified two scripts as AdThink and OnAudience, which then use the login data as an ID for a specific user, allowing them to be tracked from website to website, and in turn creating an avenue for targeted advertising. AdThink, for example, was found sending its collected information to consumer data broker Axciom, where it's likely to be added to a database on users that have visited the website running the script.
While the scripts were said to mainly focus on collecting usernames, there's no technical reason why they couldn't do the same with passwords.
Computer science professor Arvind Narayanan, one of the Princeton researchers on the project, notes that the source of the problem is websites that allow plugins like AdThink to run in the background, whether knowingly or not. "We'd like to see publishers exercise better control over third parties on their sites. These problems arise partly because website operators have been lax in allowing third-party scripts on their sites without understanding the implications."
