The 10 Most Infamous Viruses And Scams Around The Web
The internet is the most powerful communication tool of modern life, but it is fraught with danger. It seems that for every website with happy cat memes, there is a dangerous digital pathogen looking to strike and upend your digital life. We have been contending with internet scams and viruses for as long as we have used the internet (via Kaspersky). Despite a long history of raising awareness and creating tools to combat these problems, they persist.
Still, scores of harmful programs never amount to much of anything. Most people with a knowledge of coding and a bit of web savvy can produce a virus or malware, but they will also have to follow through with distributing it. Many scams come from places such as India and Nigeria due to the heavy usage of the English language while the viruses often come from eastern Europe and Asia. The rogue nation of North Korea has been known to involve state actors in a multitude of cybercrime. Regardless of origin, these events are a menace and are not likely to go away soon. As long as there are ways to cheat the system for money, there will be people willing to cheat. These are 10 of the most notorious scams and viruses from the world wide web.
Autostart worm
Today, Apple computers are seen as a premium product and are the preferred system for millions of people. This was not always the case. Up through the '90s, a huge rift between Apple and Windows users existed akin to a rivalry. This was also a time when computer viruses became a well-known threat. For many years Apple users remained relatively immune to this problem and rarely had any reason for having virus protection on their machines. This changed in 1998.
That year AutoStar 9805 began to proliferate on Macintosh computers running on the PowerPC architecture and infected them through a vulnerability in Apple's QuickTime software. The worm would install itself and run in the background, eventually destroying files. The first symptom users would encounter was a sudden restart of the computer that would happen after it had been installed into a system folder (via Indiana University).
Many companies quickly developed fixes for the worm and offered them for download, Indiana University notes. The worm was quickly eradicated but left many Mac users feeling vulnerable.
The Creeper Program
Before we had the internet, there was ARPANET, a computer network created by the Department of Defense to connect its computers that was also used by research facilities at universities (via Britannica). This was in the late '60s and early '70s before most people had ever used a computer. But for the intrepid researcher, computers were a marvel of technology that helped with calculations done in an amount of time not possible by humans. These networks were rudimentary by today's standards but were cutting-edge for their time. This early network also spawned the first computer virus.
"I'm the creeper, catch me if you can," is the phrase that many users of ARPANET found unexpectedly popping up on their screens in 1971. Bob Thomas, the creator of packet switching networks, devised a test to see how a program could spread throughout a network and at what pace. Much to his surprise, this self-replicating program did indeed infect other computers and it caused much trepidation among the managers of the mainframes in these research facilities, as this program kept replicating and popping up on other terminals (via History Computer).
Although it required a significant amount of work to get rid of it, Thomas had intended no malice as the program was just an experiment. He had proved that a program could spread easily among the computers on the network and, incidentally, created the first computer virus.
The Nigerian prince email
Most anyone who has been on the internet since the '90s has received an email from someone proclaiming to be a prince from Nigeria, having found themselves in distress due to political turmoil (via CNBC). These scams take on many forms but the basics remain similar throughout. The scams offer an opportunity for the recipient to receive a large sum of money for helping the prince liberate his cash holdings overseas and away from the people who have stolen it from him in his country. In exchange for helping, the prince will share the bounty once it is received. In some forms, the prince needs a small advance to get the fees covered to make the exchange. In others, all that is needed is bank account information to make the transfer.
No matter what form the scam takes, there are no funds just as there is no prince. Nigeria is currently a representative democracy and the most well-known of former Nigerian royalty, Prince Kunle, stepped away from royal life more than two decades ago (via Insider). Sadly, according to CNBC in 2019, this scam still exists today and is still taking as much as $700,000 away from unsuspecting victims drawn in by the allure of quick and easy money.
Popup tech support
Computers can be a frustrating piece of equipment even for the tech-savvy. For the Luddites, it can be costly. Especially for those who did not grow up with them. Problems that arise can be difficult to fix and many people rely on friends, family, and tech support to figure things out when they go awry. However, bad actors have created a scheme to artificially make things go asunder and come to their aid much like a mob boss offering protection from the mob to local businesses.
Scores of companies, mostly in India, have scripts that are embedded into websites that hijack a browser and display popup messages claiming that there is a malfunction that can be fixed by calling the number listed (via Malware Bytes). Once they have a victim on the phone, they offer to "fix" the computer for a fee, which can range from $200 to $1000. Presumably, the popup goes away once paid and victims may not even know they have been scammed. It is an insidious practice that is difficult to prosecute. The FTC has plenty of details on this scam and also offers advice to consumers on how to avoid it.
Stuxnet
Computer viruses and worms are well-known scams usted to cause malicious damage to unsuspecting users, but there are other more menacing ways to use such a program — as a weapon. Wired tells a tale that details how one of the most sophisticated computer hacks in history was meant to slow down or end nuclear research by the government of Iran.
In 2010, Iranian workers at a nuclear research facility had an issue with centrifuges randomly shutting down. This problem was also noted when computers in an unrelated facility were crashing and rebooting repeatedly. It is a long story, but the abbreviated version is that someone managed to get a malicious program into the nuclear facility on a USB drive. None of the computers were connected to a network, so the program had to be physically brought in unsuspectingly. Once installed, it targeted German-built Siemens equipment and caused multiple failures.
Nobody has yet taken credit for it, but it is widely thought to have been done by the CIA with help from Israeli intelligence services, especially because of how advanced and sophisticated this clandestine operation was, and by some governments, it is considered a digital weapon that was used to inflict damage on the Iranian nuclear facility.
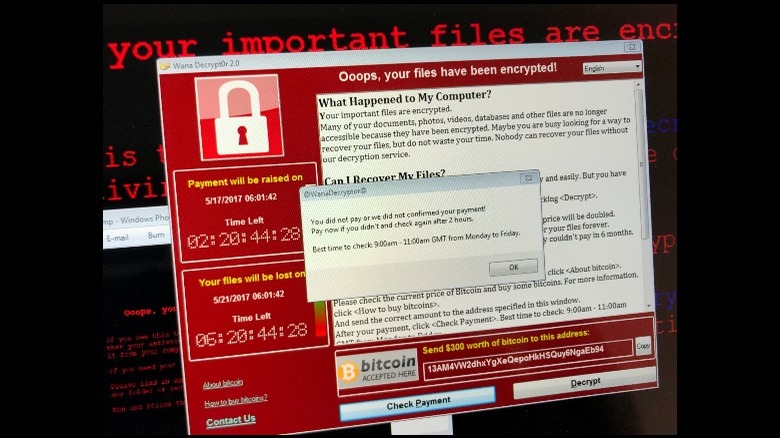
WannaCry
In 2019, malicious software infected computers across the globe and threatened the operations of some of the biggest institutions, including the UK's National Health Service, the NHS (via Kaspersky). This malware attack is a tale of international espionage by clandestine computer engineers. The malware is called WannaCry, and it is based on code developed by the National Security Agency that was, according to the BBC, subsequently stolen by hackers and sold on the dark web.
The WannaCry malware is a program that can install itself on a computer by exploiting a vulnerability in a program. Once it is installed, all or most of the files on that machine are encrypted and a screen is displayed showing a countdown timer until the program completely destroys the encrypted files with a bitcoin wallet to send payment to have the files unlocked. Tech Crunch reported that this infected many major institutions including the NHS, Spain's Telefonica, railway networks, and several municipal official government websites. Many institutions were forced to pay the ransom as they lacked sophisticated network security firms to free their networks.
WannaCry has been attributed to the North Korean government, which is said to keep a large contingent of computer professionals dedicated to malicious activity to raise hard currency for the government, and the US Department of the Treasury has sanctioned the rogue state for this act. WannaCry was also defeated by a talented computer engineer who found an exploit through an unregistered domain, according to NBC News.
The Morris Worm
Another computer worm predating today's internet was the Morris Worm. According to the FBI, this story began in 1988 when UNIX computers at UC Berkeley started to slow down to the point they became unusable. They had been infected with a new computer worm that was replicating and spreading at an alarming pace. Only computers running a certain version of UNIX were affected, but that covered many machines
Named for creator Robert Tappan Morris, the worm was created out of a sense of curiosity and quickly became something much larger than originally imagined. It exploited certain parts of the programming that enabled email but began propagating so quickly that it nearly shut down the networks of several campuses. While it was eradicated fairly quickly, the cost of doing so was substantial. Morris attempted to correct the mistake but had been thwarted by the traffic congestion caused by the initial infection of the networks. Morris ended up being indicted under a recently passed bill related to unauthorized access to computer systems and networks, thus becoming the first person ever prosecuted for a cybercrime (via History Computer).
Covidlock
Some people never let a catastrophe go to waste, and this includes scammers. While the world was suffering from the effects of the spreading coronavirus SARS-COV-2, or COVID-19, hackers were devising plots to steal money. This time the culprit was ransomware targeted at users of the Android operating system in an app that purported to track the spread of the coronavirus, as reported by Tech Republic. Instead of showing any information about COVID-19, it blocked users' access to their contacts, pictures, videos, and social media accounts until a ransom has been paid to free the information. The result of not paying the ransom is a threat to release all of the information publicly.
Users of Android phones with version 7.0 and up have better defenses against this malicious software. Domain Tools says that if the phone is protected with a password, then the risk of being infected is significantly lower. This is a reminder for all users to be vigilant about their usage of apps and to only download those that are verified from known sources.
Colonial Pipeline ransomware attack
Malware, ransomware, and viruses are extremely annoying, menacing, and insidious attacks on our digital lives. They can disrupt communication and cause damage to computer systems, often resulting in disrupted services and huge expenditures for repairs, but rarely do they cause shortages of needed commodities. 2021 marked a banner year for these malicious hacks when a particularly sophisticated attack affected the Colonial Pipeline, an oil delivery pipeline system that serves the southeastern portion of the United States.
Tech Target explains that the Colonial Pipeline moves oil from the Gulf of Mexico to refineries on the east coast through 5,500 miles of pipeline. The disruption of this supply affects not only individual drivers, but also airlines, trucking companies, and even the supply of home heating oil. After this attack happened, President Biden declared a state of emergency. A hacker group known as DarkSide gained access to the pipeline's computer systems due to a compromised password. The ransomware was then installed and encrypted the files, demanding a ransom of 75 Bitcoin in exchange for the decryption key. Colonial paid the ransom and got their systems back online within a couple of days.
The hack caused panic buying throughout the southeast and caused long lines to form at gas stations in several states. The FBI was brought in to investigate and managed to recover about 63 bitcoin, valued at $2.4 million at the time.
Overpayment scam
Sellers of goods online are susceptible to many scams from unscrupulous buyers. These scams have been around for a while and have often targeted for-sale listings on Craigslist. They are easy to spot but unsuspecting and naive sellers are prone to fall for them.
This scam works by contacting a seller and offering to pay either full price or a premium above the asking price. Then the seller is offered a check that can be deposited in their bank before shipping the product. Before closing the deal, the buyer will say the check is made out for more than the selling price with various excuses for why it is like this but then asks the seller to deposit and return the money via money order or some other certified funds before shipping the item (via Scambusters).
The checks are always fraudulent and will be returned to the seller's bank, which will then remove the funds to cover it, often leaving the seller with an overdrawn account. The Federal Trade Commission has had a warning issued about this scam since 2004 and lists ways for sellers to protect themselves.