Windows 8 security loophole demoed by researcher
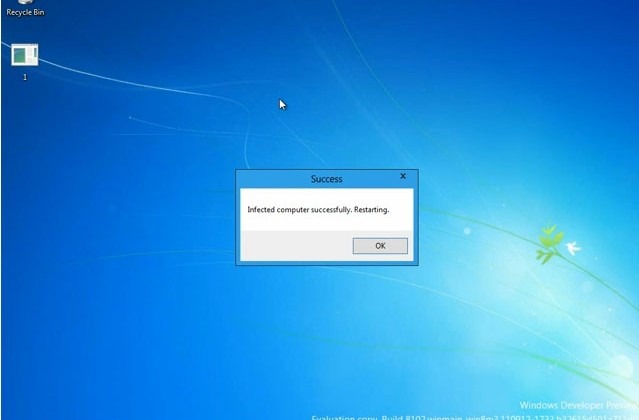
Microsoft's Windows 8 isn't due out in full until fall of next year, but security researcher Peter Kleissner has already found a way to exploit the platform. Kleissner created a Windows 8 bootkit that can bypass the User Account Control using just 14KB of exploit code. It's said to be the first proof-of-concept to find a vulnerability in Windows 8 and he's posted a demo video of the process.
The exploit works on the current Windows 8 developer preview version, allowing a hacker to run command prompts under the SYSTEM account once exploited. It bypasses the User Account Control completely and does not prompt the end user. This appears to be an extension of the Stoned bootkit that Kleissner developed as a proof-of-concept to to exploit Windows XP, Vista, and 7 as well as Windows Server 2003.
The issue will likely be addressed by next year's launch, but it does show that despite Microsoft's already beefed up security for Windows 8 that there's still plenty of work ahead. Microsoft is stepping up the security with its Windows Defender for Windows 8 to include real-time detection and protection from malware through a file system filter. Windows 8 will only boot properly signed and validated code and will have an improved SmartScreen filter, extending its browser security features to the entire platform.
[via WinRumors]