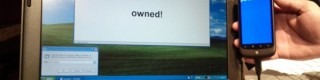
USB smartphone exploit turns Android into an invader
Next time somebody asks you if they can recharge their smartphone from your laptop's USB port, you might be opening yourself up to a potential malware attack. Professor and student team Angelos Stavrou and Zhaohui Wang from George Mason University have figured out a system whereby a compromised Android smartphone mounts as a standard HID (human input device) when plugged into a Windows, OS X or Linux computer, potentially giving keyboard and mouse access to malware or even a remote hacker.
Because the new device installation happens automatically – and with little in the way of notifications or ways to prevent it from taking place – users might not spot that the phone is loading as more than just a mass-storage device. Although the proof of concept was done with a modified Android kernel, it could just as easily be modified to run on iOS devices like the iPhone 4.
"Say your computer at home is compromised and you compromise your Android phone by connecting them. Then, whenever you connect the smartphone to another laptop or computing device I can take over that computer also, and then compromise other computers off that Android. It's a viral type of compromise using the USB cable" Angelos Stavrou
Device contamination could come from a downloaded app or browser exploit, or it could be spread by plugging a clean device into an infected computer; Stavrou says it will also work with direct USB connections between smartphones. Meanwhile antivirus software wouldn't necessarily spot the malware in action, because it would appear to be normal keyboard/mouse activity. The duo presented their research this week at the Black Hat DC conference.
[via Android Community]