Russian spy caught snooping on Facebook traffic using Tor exit nodes
Two researchers were recently using custom software to test out Tor exit nodes for suspicious behavior and discovered something interesting. The researcher spent four months studying Tor exit nodes and found that somewhere in Russia a network of wiretapped exit nodes exists and the person or persons operating them are particularly interested in Facebook use.
The researchers are Philipp Winter and Stefan Lindskog from the University of Sweden. The two researchers identified 25 nodes that are tampering with web traffic, stripping out encryption, or censoring websites. The team believes that out of those 25 nodes, a handful are the result of configuration mistakes and ISP issues.
However, the researchers say that 19 of those nodes were caught using fake certificates to perform man-in-the-middle attacks. Those nodes were decrypting and re-encrypting traffic that passed through on the fly. The researchers also say that at certain times those nodes were only intercepting traffic to particular sites like Facebook.
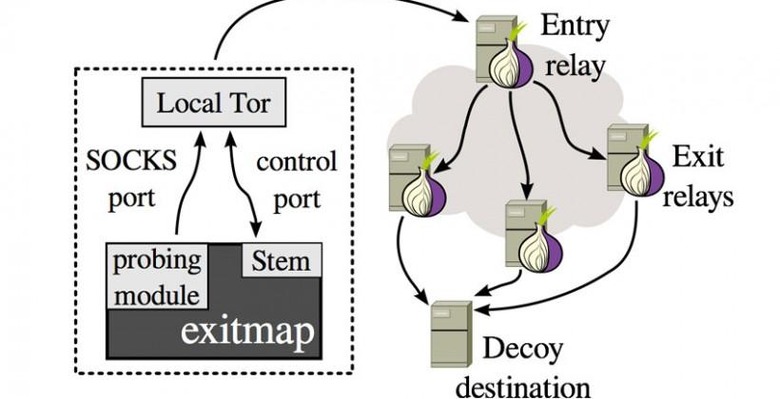
The researchers also note that there may be more nefarious nodes that they didn't find during their research. Tor is a free software platform that helps users to surf the internet with anonymity. The Tor network has over 1000 exit nodes that traffic is dumped through after the traffic is bounced around to anonymize it.
The exit nodes are where the Tor traffic is vulnerable according to the researchers. Tor nodes are run by volunteers and therefore subject to bugging. The researchers also note that when they had the nodes blacklisted that were using bogus certificates, other nodes using the same certificates opened shortly after. Tor traffic may not be as anonymous as users think.
SOURCE: Wired