Microsoft swats Russia's Fancy Bear with ingenious legal takedown
It's time for Putin's hackers to be on the receiving end of the beatdown stick of digital attacks this week. The folks behind the attack come from Microsoft, and the Russian hacker team goes by the name Fancy Bear. Yes, Fancy Bear, a name that's brought relative shame to the Democratic National Convention's game, also known as the Kremlin's cyber spy team. But Microsoft isn't attacking with "the cyber" – they're attacking with... the law!
Microsoft's legal team is rolling deep with lawsuits aplenty, a bunch of which were originally filed back in 2016, with actions starting well before this in years past. Microsoft sued the hacker group itself in federal court with accusations of cybersquatting, computer intrusion, and infringing on Microsoft-owned trademarks. The full legal documents – those made public – can be found at Notice of Pleadings.
FBI and CIA agree: Russia hacked USA to benefit Trump
The trademark business is the most interesting of the whole stack of legal documents – if not the strangest. In the filing, Microsoft says the defendant (John Does 1-2) was illegally "controlling a computer network thereby injuring plaintiff and its customers." The trademarks listed in the filing are as follows:
• 2165601 – Hotmail (service mark)
• 2277112 – Internet Explorer (trademark)
• 2463526 – Windows (service mark)
• 2872708 – Microsoft (service mark)
• 4941897 – Microsoft OneDrive (service mark)
• 4255129 – Outlook (service mark)
Microsoft filed the Hotmail trademark back in 98'. VIA the USPTO we learn that inside the listing for the Hotmail trademark, Goods and Services claimed are: "promoting the goods and services of others by placing advertisements and promotional displays in an electronic site accessed through computer networks and by delivering advertisements and promotional materials to others via electronic mail." As such, if someone in Fancy Bear uses Hotmail to deliver malware, they're potentially in violation of Microsoft's (long since granted) trademark filing.
A similar situation goes down with a Windows trademark. In the 2001 registration of the service mark Windows, Microsoft describes Windows' goods and services as follows. "Providing information over computer networks and global communication networks in the fields of entertainment, music, and interactive games; education services, namely on-line tutorials in the field of computers and computer software."
If the Fancy Bear crew use their big fat paws with Windows to cause harm to Microsoft and/or their customers, they can be sued. And that's exactly what Microsoft did – and continues to do.
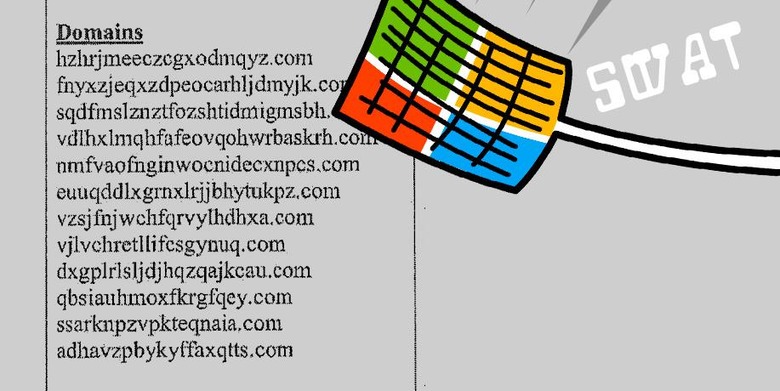
One of the results of these legal moves by Microsoft is the re-assigning of domain names previously used by Fancy Bear. The domains that appeared in the court filings are, by and large, completely bonkers. Or bonkers at least to the naked eye, anyway.
Once Microsoft successfully turns these domains out – and has them redirected back tot heir own nameservers – Fancy Bear is out of luck. As the Microsoft filings suggest, "Microsoft alleges that Defendants have violated Federal and state law by hosting a cybercriminal operation through these Internet domains, causing unlawful intrusion into Microsoft and Microsoft's customers' computers and computing devices; and intellectual property violations to the injury of Microsoft and Microsoft's customers."
Particularly effective in this case is the following notification by the court: "NOTICE TO DEFENDANT: READ THESE PAPERS CAREFULLY! You must "appear" in this case or the other side will win automatically." As such, Microsoft is winning.
Sort of. Microsoft nor the courts have been able to reach any Fancy Bear hackers, nor have they been able to track them in any way that's lead to a real, actual human being. According to payment records cited by The Daily Beast, the Fancy Bear team only ever registered domain names with burner credit cards or BitCoin (which is also untraceable in its transaction origins by definition). Server logs were similarly difficult to trace due to the hackers making use of Tor – AKA The Onion Router, or the dark internet.
