Malware can hijack Firefox extensions to compromise users
Web browsers these days, especially Chrome, use sandboxing methods to prevent unauthorized access to the computer or excessive use of resources. But while that may be true for the browser's tabs and content themselves, that might not always apply to other things related to it, like extensions. That is the problem facing Firefox and some of its most popular extensions right now. Security researchers have discovered that thanks to vulnerabilities in how Firefox implements extensions, hackers can write seemingly harmless add-ons that piggyback on "clean", valid extensions in order to gain access to files or scam users.
Web browser extensions have become more than simple add-ons. They sometimes become the determining factor in the current age of the browser wars. And, to some extent, those extensions are indeed critical in providing functionality that browser makers either don't have to implement or are completely not interested in implementing.
Sadly for Firefox, those extensions have today become a liability as well. The problem is that these extensions do not run sandboxed and are able to actually access data or functions from other extensions that are also enabled. This could mean, for example, that a malware masquerading as an add-on can access the functionality of one add-on to get access to system files or the ability of another add-on to redirect users to a certain web page, usually a phishing scam page. In the eyes of Mozilla's automated security checks, the devious add-on is blameless as it does nothing out of the ordinary.
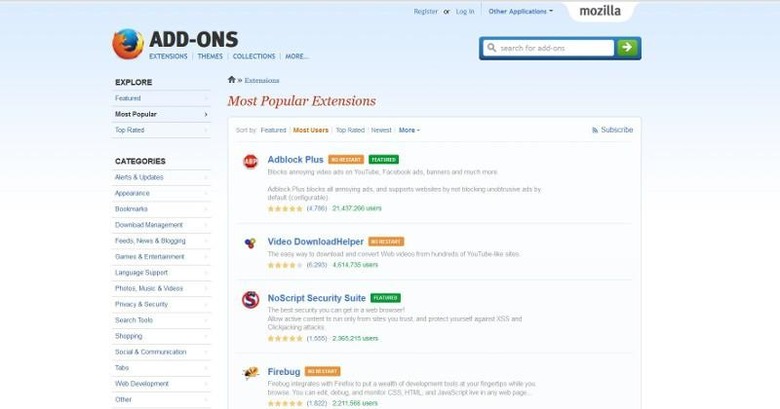
Most of the time, problematic extensions are the "shady" ones. This time, however, nine of the top 10 Firefox extensions have been found to be vulnerable to this type of process. That includes extensions like AdBlock Plus, Video DownloadHelper, NoScript, and even developer tools like Firebug and Greasemonkey.
Firefox's VP of product has acknowledge that the issue does exist and that developers are working towards plugging up that hole. Its new set of WebExtensions API, which are already available, implement safeguards against that kind of attack. Firefox will also be sandboxing extensions to prevent such scenarios from happening in the first place.
VIA: Ars Technica