Gmail security gets new spy warning, Safe Browsing alerts
Google is rolling out additional security features in Gmail, boosting the information users get about any nefarious activities that are going on. As well, the Internet giant has also teamed up with some other big players like Microsoft and Comcast to submit a draft IETF specification for "SMTP Strict Transport Security," says Google. This is in response to an issue it sees with email encryption — namely, there are ways someone could "still tamper with" email encryption even if the user is sending mail over an encrypted connection.
Google detailed its latest efforts today, first pointing toward the red lock icon it added to gmail, making it easy for someone to visually tell whether a message was sent using encryption. Google says the feature has worked well, with number of emails being sent over an encrypted connection jumping 25% since the lock was rolled out.
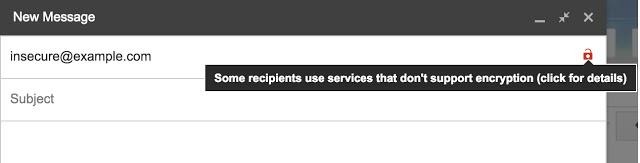
The Internet giant says it has identified a different area that needs addressed, though — namely that someone could tamper with email encryption is something has been misconfigured, or using "malicious parts of the Internet." The company wants to help make sure TLS encryption works, and so it has sent a new proposed standard with partners Yahoo, Comcast, and Microsoft.
That issue aside, Google is also expanding the use of Safe Browsing in Gmail, saying that this week and henceforth, users will see warnings advising them they're about to visit a dangerous website (assuming they click a link leading to an insecure site).
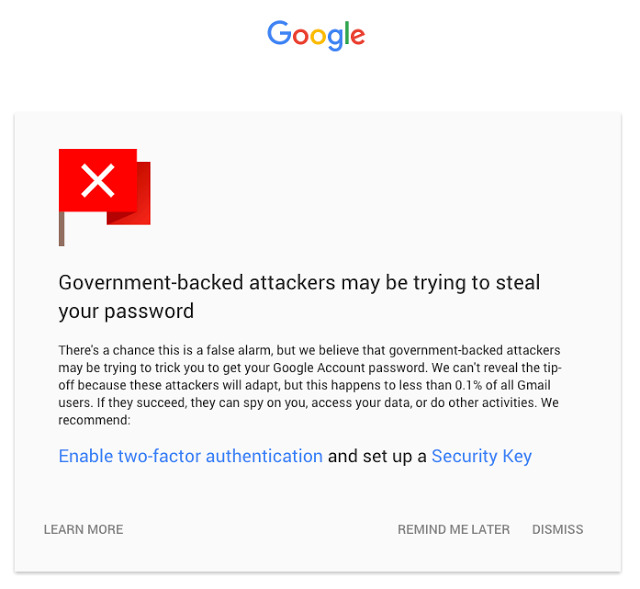
Finally, Google has decided to ramp up its state-sponsored notifications inside Gmail, something it first rolled out back in 2012. When applicable, the company notifies users if they're the target of state-sponsored attackers, something Google says affects less than 0.1% of its users. When someone does get the warning, though, it is very important they pay attention, and so Google is launching a new full-page warning with details on what users can do to help keep their data safe.
SOURCE: Google Security Blog
