Android SoC security keys extracted: Qualcomm TrustZone in question [UPDATE]
A security exploit appears to have been discovered which allows smart devices (mostly Android) with Qualcomm processors to be hacked into easily. This story began as documented on the blog Bits, Please back in April of 2015, when user "laginimaineb" decided to reverse-engineer Qualcomm's TrustZone implementation on Snapdragon processors. Using a Nexus 5 smartphone, this user detailed "a chain of vulnerabilities that I've discovered which will enable us to escalate our privileges from any user up to the highest privilege of all – executing our code within TrustZone itself."
TrustZone is a technology that exists in ARM processors – more specifically a set of security extensions for ARMv6 (and above) processors that create a sort of second lock for your password(s). It's a place where a keys are stored that nobody knows save the system. You don't know them, software makers don't know them, and hardware manufacturers don't know them. They remain secure in your smartphone, able to be seen by nobody save the processor itself.
Does your device have a Qualcomm Snapdragon processor inside? Probably yes. Have a peek at their Qualcomm Device Finder to see!
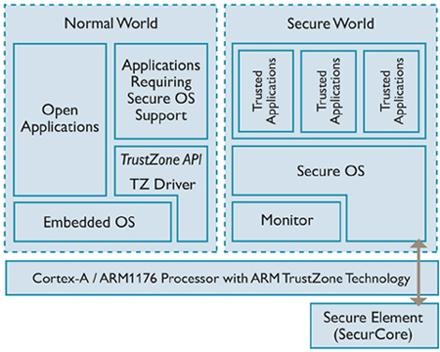
As listed by ARM itself, the following items can be used in concert with the TrustZone:
• Firmware protection
• Security management
• Root of trust implementation
• Peripheral and I/O protection
• Code isolation between multiple suppliers
• Sandboxing for devices with certified software
• Consolidation of multiple helper processors into one
User laginimaineb posted on Twitter about his discovery – Qualcomm KeyMaster keys directly from TrustZone.
This is good and bad.
Good for developers who want to modify their Android smartphones at a deeper level than what's been available ever before. Android smartphones with Qualcomm processors can have their bootloaders unlocked more easily, unsigned images could be booted to these phones, etc.
Bad because with that access, security features like Full Disk Encryption (FDE) will be easier to break and/or bypass. Reddit user OFTN explains:
"Full Disk Encryption is now much easier to bypass on many devices until this gets fixed. There are a few other things that rely on this, but FDE is the most important. This is where your encryption key is stored. Your encryption key is itself encrypted by the password you enter to decrypt your device (your password decrypts a bigger more reliable password essentially), so if you don't have a very long and secure password, it is now easy to break FDE, as an attacker won't be limited by a limited number of password attempts."
"Attackers can extract your key and brute force your password using it."
In the past, laginimaineb has suggested via Hacker News that he's "responsibly disclosed to Qualcomm" his activities – in that case a "vulnerability that I've discovered which allowed complete arbitrary code execution within TrustZone." Until we hear back from him and/or Qualcomm, we can only cross our fingers that the method being used this month has been patched.
UPDATE, 10:42 AM Central Time: According to laginimaineb, "I've disclosed all the vulns involved, and am letting [Qualcomm] preview the blog post before I release it."UPDATE 2, 2PM: User laginimaineb suggests that the vulnerability is "100% patchable" and reminds us that he's "disclosed all the vulns involved."UPDATE 3, 10PM: Qualcomm has provided the following statement to SlashGear: "Providing technologies that enable robust security and privacy is a top priority for Qualcomm Technologies, Inc. (QTI). QTI works proactively to identify and address security vulnerabilities in its software. The TrustZone security vulnerability in question (CVE-2015-6639) had already been identified and addressed and a patch made available to QTI customers."
